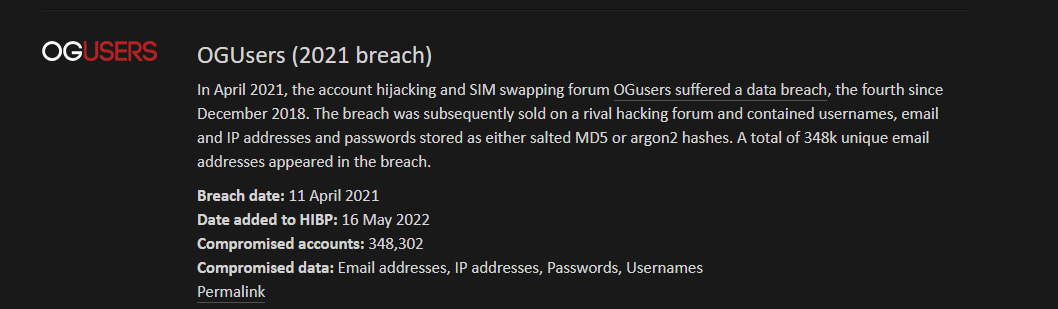
Why should we use a fake email?
The most common attack vectors used by the threat actors to compromise the target system is the phishing attack or spam. The phishing attack consist of sending a malicious email to a target, once the target receives and clicks on the message (open a link or attachment), the threat actors could then compromise the system. They are many websites that require to register before using it, some of these websites could be owned by the threat actors or could be sending annoying advertisement every time to you. To avoid this issue, the appropriate solution is the use of “fake email”.
A fake email or email generator is an email address generator used to create an email address that is used to receive a message. The Fake email will help you to protect your email address from receiving spam, phishing, advertisement from third party, avoiding detection during investigation for example instead of using your company email to test a suspicious website, you can use a fake email.
There are many fake emails freely available over the internet.
Temp Mail - Disposable Temporary Email (temp-mail.org)
Temp mail is an open source used to receive for certain amount of time. You can use the service to register to a website and get the notification code or activation code from the Fake email. The technology will help you to protect your work email, your private email from being disclosure on a suspicious website or receiving advertisement that you do not wish.
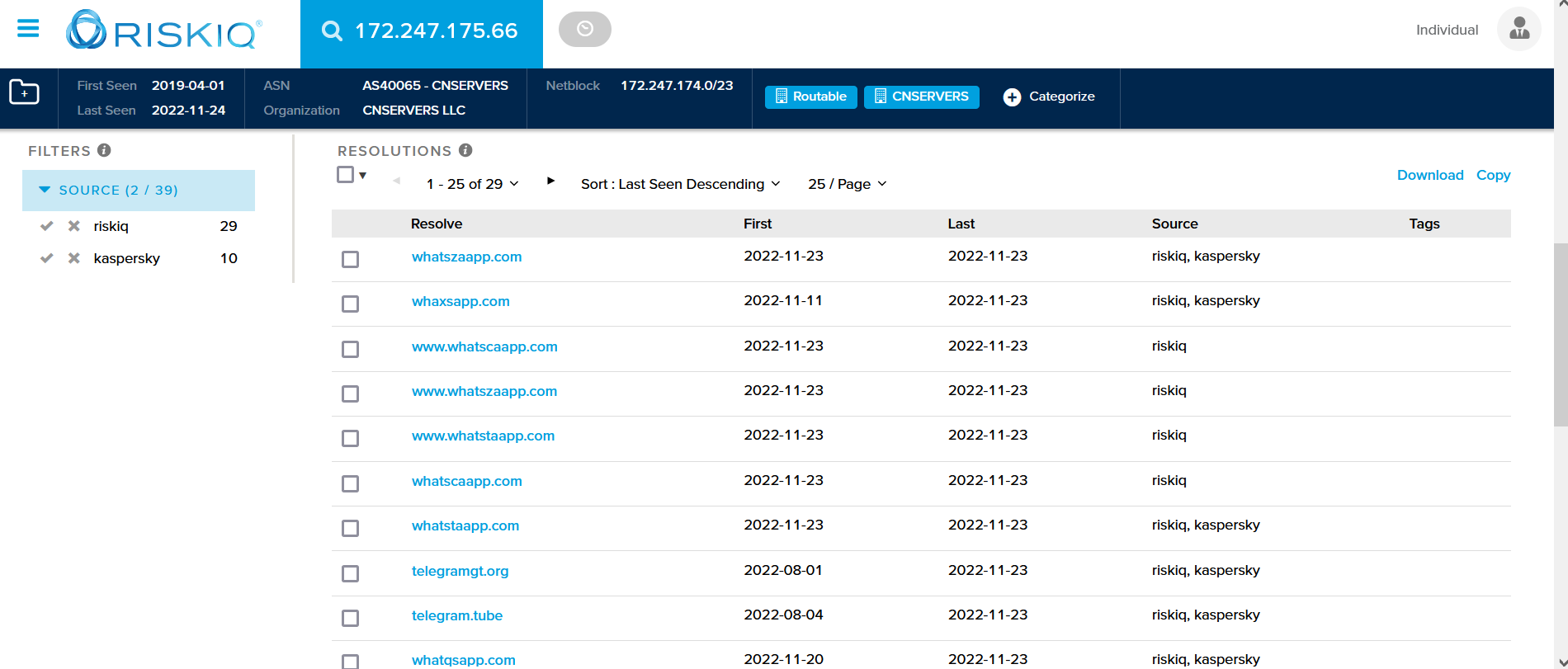
In the pictures below, we will describe the features available on the Temp mail.
Once you connect to the website, you will see the interface with the email generated for you.
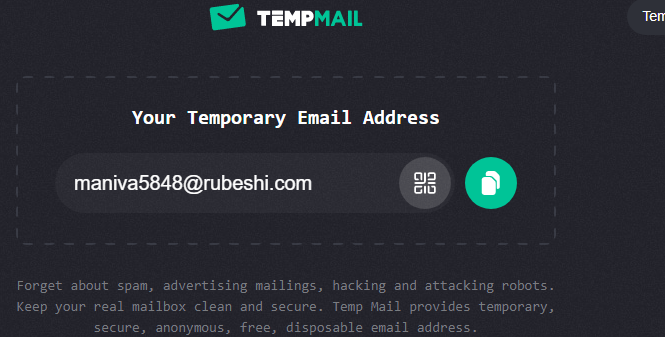
Click on the copy button to copy the email generated, submit it to the website you wish to register, within a couple of the you will receive the mail confirming your registration.
When you receive the activation code, you can then activate it and connect to the website.
Be aware that the email is used for temporary purpose.
The second option is - Fakemail
FakeMail | Temp Mail Addresses
Once you connect to the website, you will see the email address generated, the time set available to use the email and the random generated password for you to use on the website on which you want to connect.
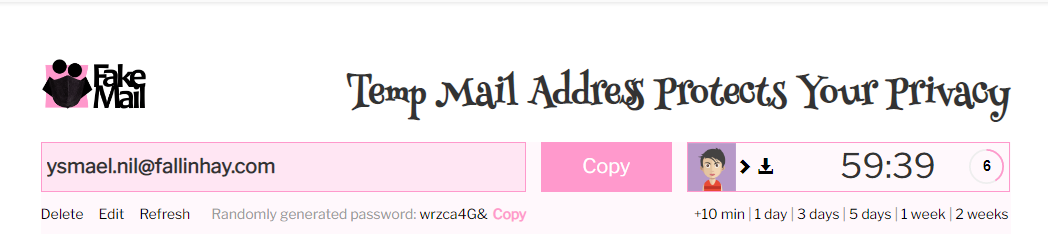
Fakemail can be used maximum for 2 weeks, so in case you have a website that you wish to reconnect again, this option is the one you can use.
The last option, we will talk about is the - email-fake.com
Fake Email - Disposable Temporary Email (email-fake.com)
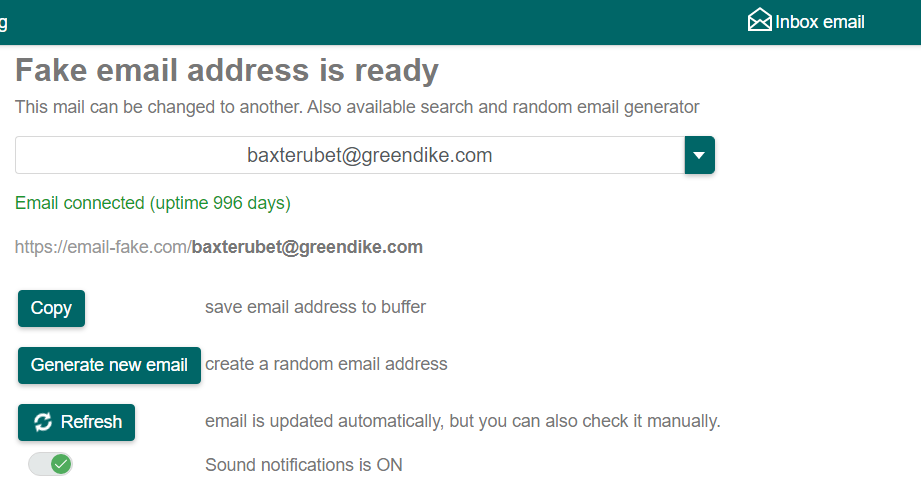
If you want to keep connected with the email for long period of time, this option is the best option. you need to choose the email you want to use, and the uptime period will be set.
Click on the arrow in “green” you will the uptime time for each email you choose.
Constrains related to email generator or fake email:
The email generator has some limits. Some websites such as Twitter, Facebook, Instagram do blacklist such email address so using the fake email to register will not be possible. In order to avoid that problem, you can use a private domain and bind it to the fake email.
A private domain is a domain that you already acquired, or you own after buying it.
To bind a domain to a fake email, once you own a domain, you need to add a DNS mail exchange on it and connect to your Temp Mail account.
For more details, visit: Private domains. How to get your own Temporary Email (2021) (temp-mail.org)
As we described, the fake email is a best practice that people should be aware of and use when needed. The protection of the data is becoming much more difficult so the best way to stay safe it to be protected. Be aware that some fake email could be owned by the threat actors so before using it make sure that it's a safe one.