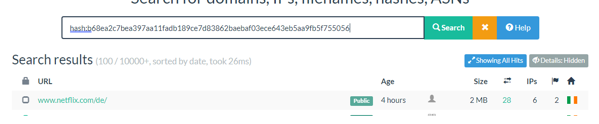
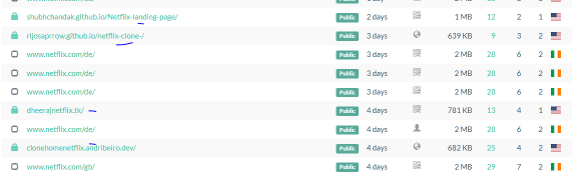
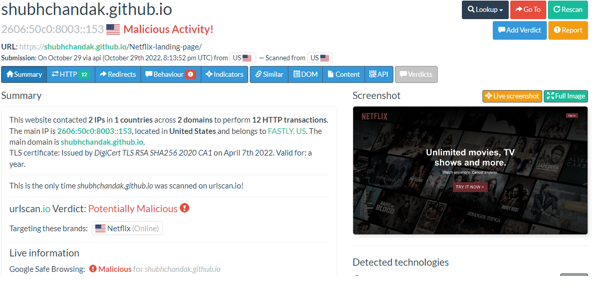
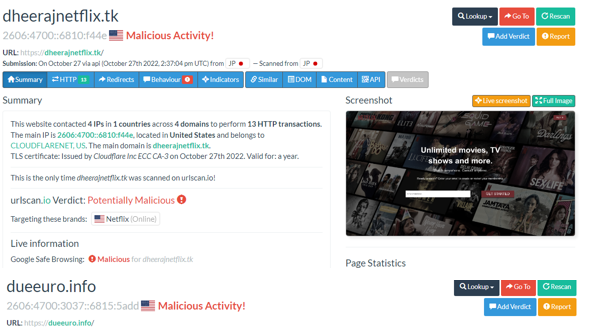
Citrix and Citrix ADC released patches for Citrix Gateway

Three Vulnerabilities have been discovered in Citrix Gateway and Citrix ADC.
The vulnerabilities are the following:
- CVE-2022-27510 Unauthorized access to Gateway user capabilities
- CVE-2022-27513 Remote desktop takeover via phishing
- CVE-2022-27516 User login brute force protection functionality bypass
Be aware that only appliances that are operating as a Gateway (appliances using the SSL VPN functionality or deployed as an ICA proxy with authentication enabled) are affected by the first issue.
The affected versions are the following:
- Citrix ADC and Citrix Gateway 13.1 before 13.1-33.47
- Citrix ADC and Citrix Gateway 13.0 before 13.0-88.12
- Citrix ADC and Citrix Gateway 12.1 before 12.1.65.21
- Citrix ADC 12.1-FIPS before 12.1-55.289
- Citrix ADC 12.1-NDcPP before 12.1-55.289
The released applies to customer-managed Citrix ADC and Citrix Gateway appliances. Customers using Citrix-managed cloud services do not need to take any action.
Recommendation:
Install the relevant updated versions of Citrix ADC or Citrix Gateway.
NB: Only Citrix ADC and Citrix Gateway versions prior to 12.1 are EOL and customers on those versions are recommended to upgrade to one of the supported versions.