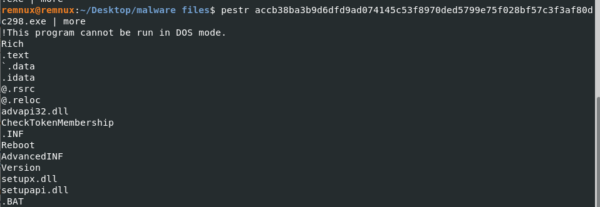
How to analyze IOCs before and after a cyber-attack
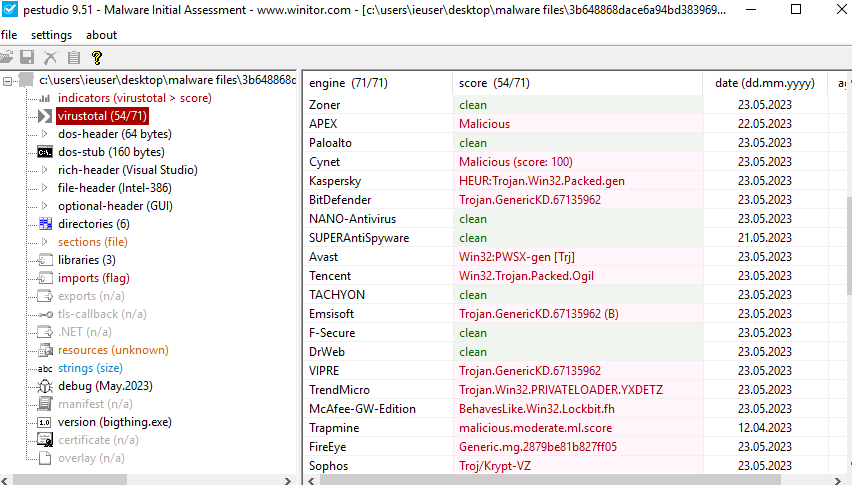
On June 27, JumpCloud discovered an APT attack. The company’s IR shared some IOCs to allow the customers or others third parties to protect their infrastructure.
As a Security Analyst, you should pay attention to the IOCS provided https://jumpcloud.com/support/july-2023-iocs .
The purpose of this article is to help the Analyst to detect and investigate different IOCs such as domains and IP addresses before or after an attack occurred.
Having a look at the domains from the list of IOCs, the first impression that would come in your mind is to check if the domains are FP or not.
Example of some Domains from the IOCs:
nomadpkgs[.]com
centos-repos[.]org
datadog-cloud[.]com
toyourownbeat[.]com
datadog-graph[.]com
centos-pkg[.]org
primerosauxiliosperu[.]com
zscaler-api[.]org
nomadpkg[.]com
As you see, some of the domains name are quite similar to the names of well-known service providers , companies for example we can observe some domains names with the name of some service providers such as Zscaler, Centos . As an Analyst, you should always be able to check such suspicious IOCs before making any conclusion.
Let’s take the example of a few domains:
zscaler-api[.]org
https://www.virustotal.com/gui/domain/zscaler-api.org/details
Whois Lookup
Administrative city: REDACTED FOR PRIVACY
Administrative country: REDACTED FOR PRIVACY
Administrative state: REDACTED FOR PRIVACY
Create date: 2023-06-23 00:00:00
Domain name: zscaler-api.org
Domain registrar id: 1068
Domain registrar url: http://www.namecheap.com
Expiry date: 2024-06-23 00:00:00
Name server 1: dns1.registrar-servers.com
Name server 2: dns2.registrar-servers.com
As you see, the result from Virustotal shows that the domain is a newly created, this is the first hint for us. As we know, most of domains used by threat actors are newly created. As Zscaler is a well-known brand, we can check the main domain of Zscaler to make a comparison between the both domains.
zscaler.com (Zscaler legitimate domain)
https://www.virustotal.com/gui/domain/zscaler.com/details
After checking the main domain of Zscaler (zscaler.com), we can observe that the zscaler.com is located at (Subject: C=US 2.5.4.15=Private Organization 2.5.4.5=4431830 L=San Jose O=Zscaler, Inc. ST=California 1.3.6.1.4.1.311.60.2.1.2=Delaware 1.3.6.1.4.1.311.60.2.1.3=US CN=www.zscaler.com )
Whois Lookup gave the following details:
Admin Country: US
Admin Organization: Zscaler, Inc.
Admin State/Province: CA
Creation Date: 2008-07-14T22:12:34+0000
Creation Date: 2008-07-14T22:12:34Z
DNSSEC: unsigned
Domain Name: ZSCALER.COM
Domain Name: zscaler.com
With this information, we can assume that the domain zscaler-api[.]org is not from Zscaler.
NB: It is always a good practice to check the browser search such as Google or Bring search to get some information about the domains.
The second example are the two domains nomadpkg[.]com and nomadpkgs[.]com
In this example, we will type the domain nomadpkg[.]com on Google search if we can find any related information, by doing that, we found a similar domain nomadpackaging.com a packaging website.
https://whois.domaintools.com/nomadpackaging.com
Dates 6,355 days old
Created on 2006-02-22
Expires on 2024-02-22
Updated on 2023-02-08
After checking the two domains, we found out that they are newly created
https://whois.domaintools.com/nomadpkg.com, https://whois.domaintools.com/nomadpkgs.com and no specifics information were found about them over the internet.
At this point, based on the naming convention, we may assume that the domains are probably mimicking the nomadpackaging.com. But for us, it is a hint for us to block such domain.
You can use the same technics we showed to analyze others domain such as centos-pkg[.]org and centos-repos[.]org or domains mentioned in the list.
NB: One thing to mention, during our investigation, we found a link https://www.usom.gov.tr/url-list.txtAlt where most of the domains available in https://jumpcloud.com/support/july-2023-iocs were reported as malicious one. You can use this link to upload the domain in your SIEM tool in order to monitor any interaction with any of them.
Now, lets analyzed some IP addresses detected during the investigation:
https://jumpcloud.com/support/july-2023-iocs
66.187.75.186
104.223.86.8
100.21.104.112
23.95.182.5
78.141.223.50
116.202.251.38
89.44.9.202
192.185.5.189
Most of the IP addresses mentioned above, look normal, seeing such traffic in your network, it is very difficult to guess that, it could be used by a threat actor. But you can use some technics to find more information about a specific IP address.
Let’s start:
In this case, a tool like https://www.abuseipdb.com did not help that much as the IP addresses look normal and most of them were not reported of any abuse, then we check the tool like https://securitytrails.com/ to list the domain behind the IP address.
By checking the domains on the IP address, we found the domain toyourownbeat[.]com (one of the domains mentioned above) address hosted on the IP address
https://securitytrails.com/list/ip/192.185.5.189
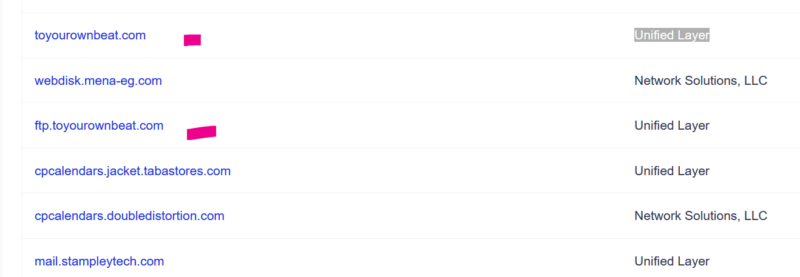
We found on the subdomains of toyourownbeat[.]com:
webmail.toyourownbeat[.]com
mail.toyourownbeat[.]com
Which could be a sign of phishing message sends to different users that interact with the website.
https://securitytrails.com/list/apex_domain/toyourownbeat.com .
I know this is a time consuming, but it is better to consume a time to analyze one indicator than to be hacked because of not analyzing it. Always stay focus and be patient.