Million of MTN Group users data available on DarkWeb by unknown threat actor
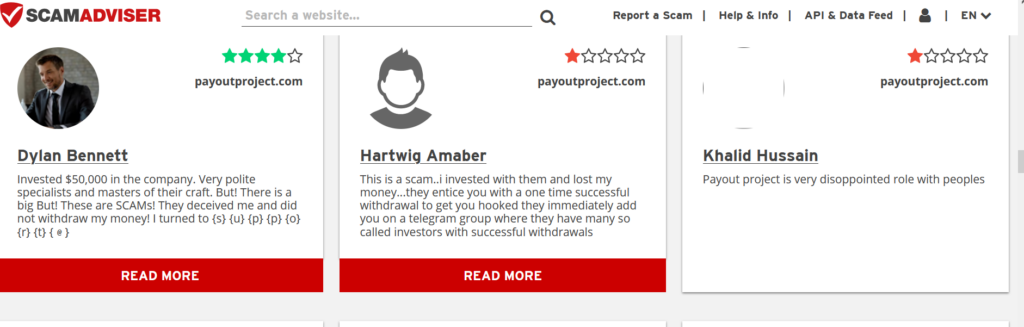
MTN Group disclosed a data breach. The company is active in many countries such as Ivory Coast, Guinea, Iran, Benin, Liberia, Nigeria, Sudan and the sponsor of the CAF Champions League football competition, Manchester United F.C and others.
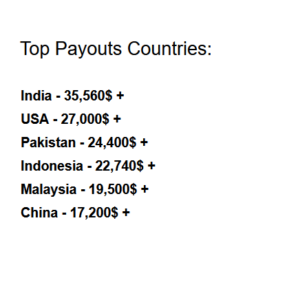
The company has million subscribers and users the data breached could impact have a huge impact if the threat actor starts targeting the users.
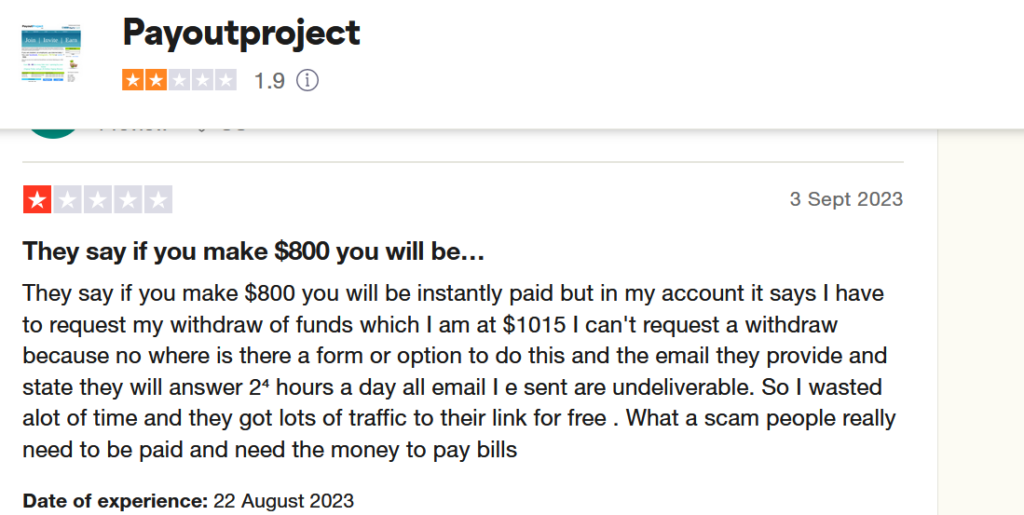
The company confirmed from their website that an unknown third-party has claimed to have access data linked to parts of their systems. The company does not have any information to suggest that customers’ accounts and wallets have been directly compromised.
The following mitigations recommendations have been put into place for the customers to remain vigilant (MTN cybersecurity incident, but critical infrastructure secure | MTN.com):
Keep MTN, MoMo and banking apps and devices updated.
Use strong, unique passwords for accounts and change them regularly.
Be cautious of unexpected messages and do not click on suspicious links.
Do not disclose information such as passwords, PINs and OTP when asked to do so by phone, text message or email.
Where multifactor authentication is available, it should be activated.
The threat actor and the source of the breaches are not disclosed yet. As a customer, we encourage you to follow the recommendations.
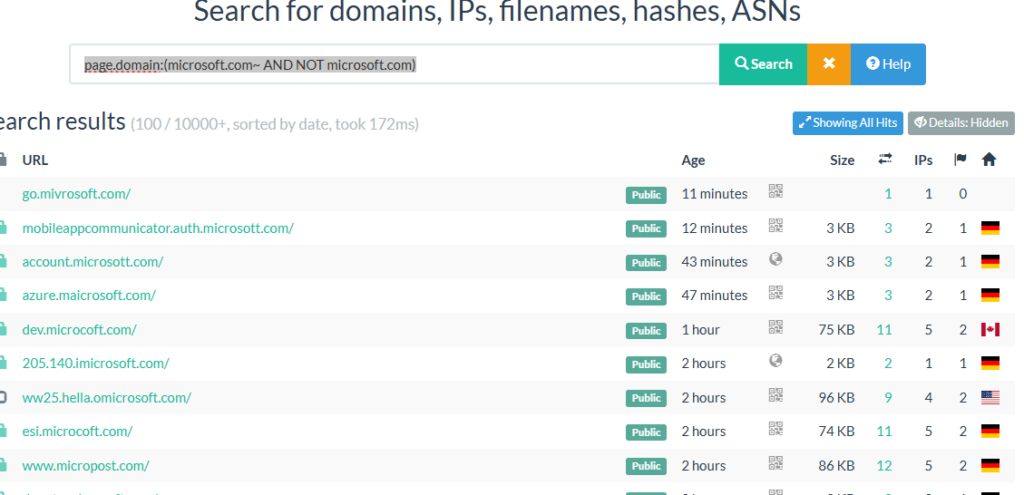
 Best OSINT tools to investigate Typo squatting domains
Best OSINT tools to investigate Typo squatting domains  Top Free Threat Intelligence Feeds for SOC
Top Free Threat Intelligence Feeds for SOC  Best WordPress website scanner for free
Best WordPress website scanner for free  Phishing as a service platforms used by threat actors
Phishing as a service platforms used by threat actors  Fake Microsoft Teams website to deliver malware
Fake Microsoft Teams website to deliver malware