How to use URLSCAN
URLSCAN is used to perform different types of web scan and also to analyze different IOCs such as IP address, domains, Hashes, filenames and others.
URLSCAN is a tool used by different security teams such as Security Analyst, Cyber Threat Intelligence, Threat Hunting, Incident response team and others.
The tool is divided in 2 versions (community version and paid version).
We will talk about the community version that is available for free.
In order to connect to the Web application, you need to type the domain (urlscan.io), once you connect to the domain, you will get to the following screen.
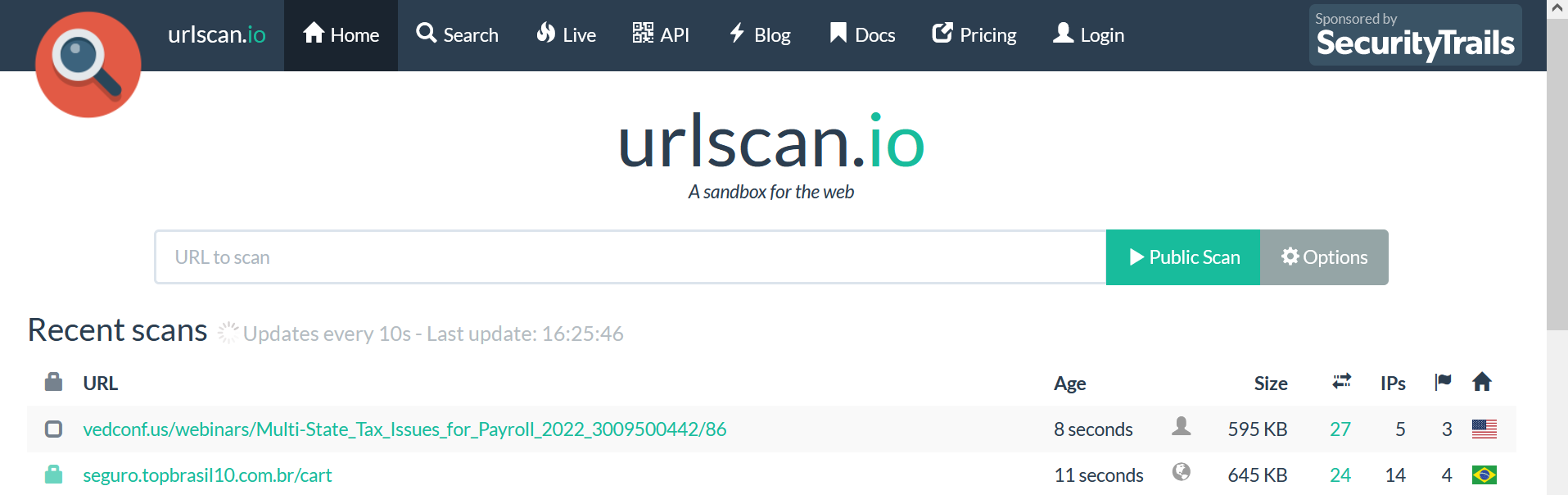
In our case, we need two menus (Home and Search)
- HOME
Once we click on this menu, we can see the scanned queried by the users from different locations.
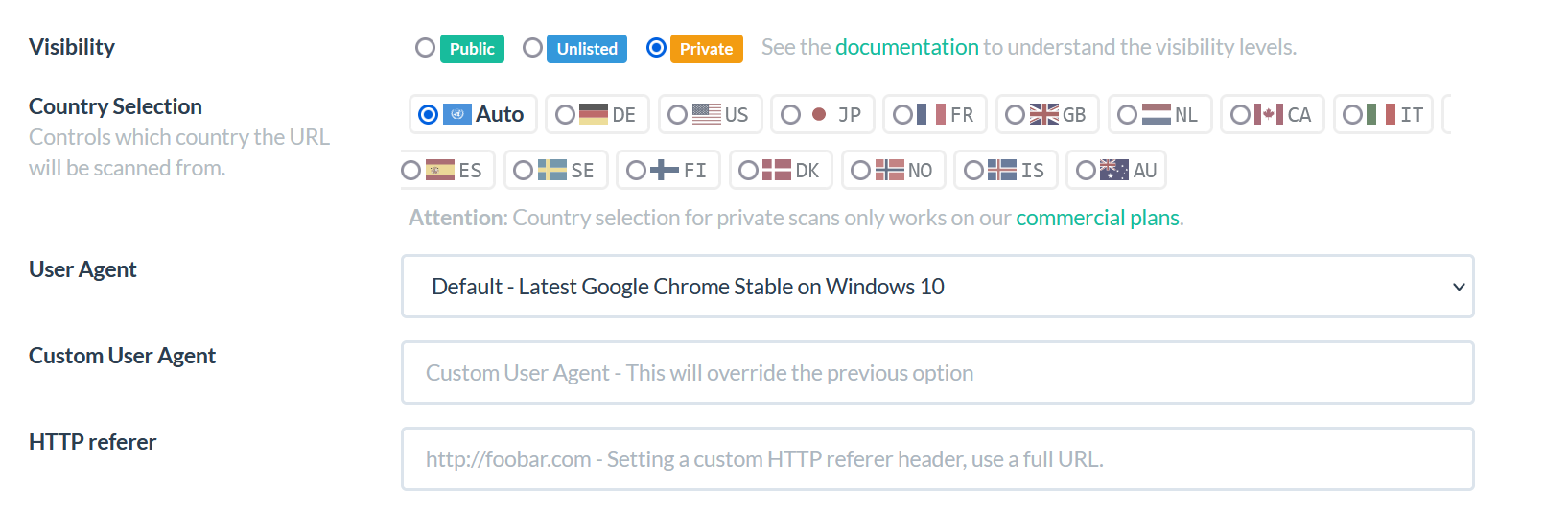
By default, the tool is showing the public scan mode, if you want to leave the default mode and scan anything, the scan will be visible by everyone.
So, we advise you to click on option and used the private mode if you do not want other people to see the query you entered, this option can also help to avoid alerting the threat actor about your findings.
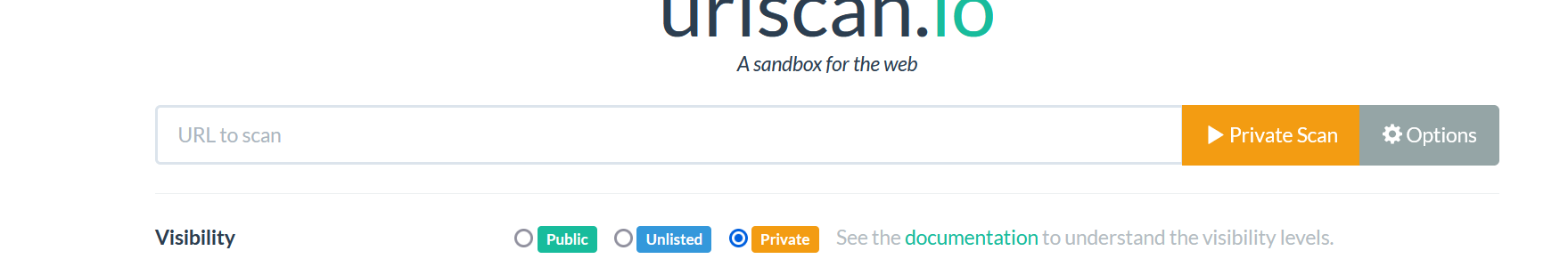
URLSCAN can anonymize your identity.
Examples:
- If you want to hide your location, you can click on “country selection” or auto (be aware that the Country selection for the private mode works only on the Commercial plans.)
- You can change the “User Agent”. For example, if the website you want to scan is for the mobile phone – you can choose one of the Android User Agent.
You can also customize your own User Agent.
- The “HTTP referer” can be used to custom the HTTP header before scanning.
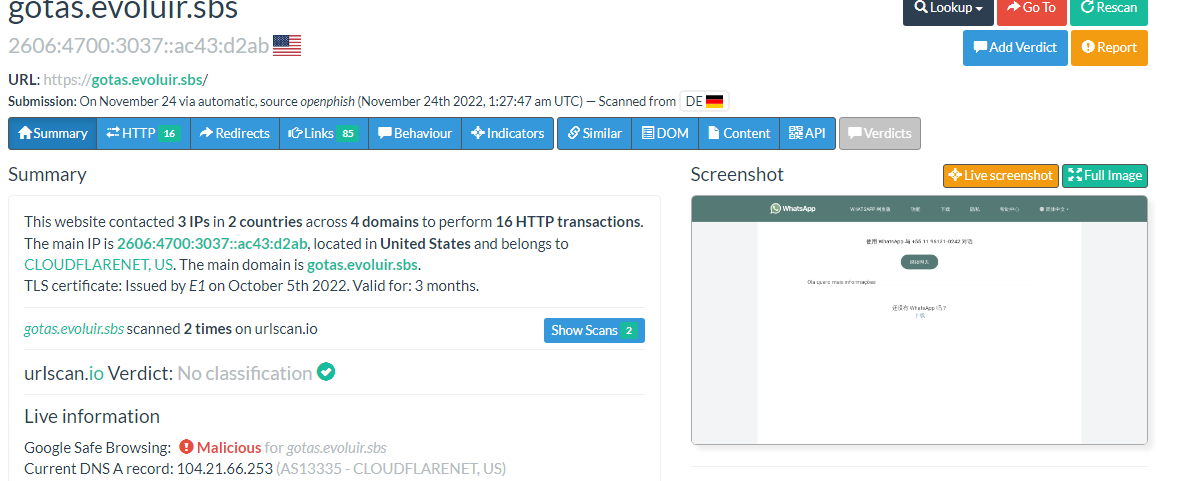
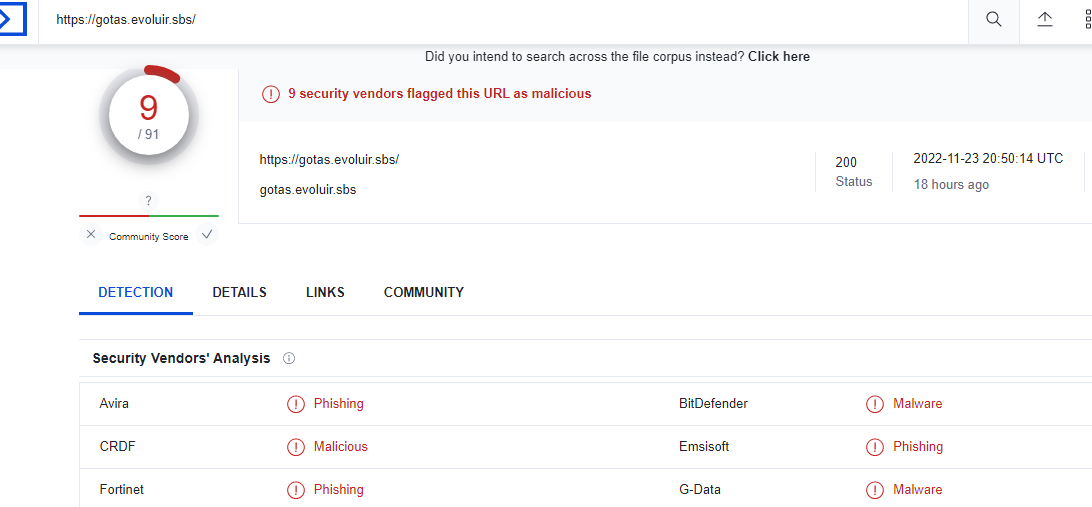
Now, lets scan in a private mode a URL in hazard and analyze its behavior.
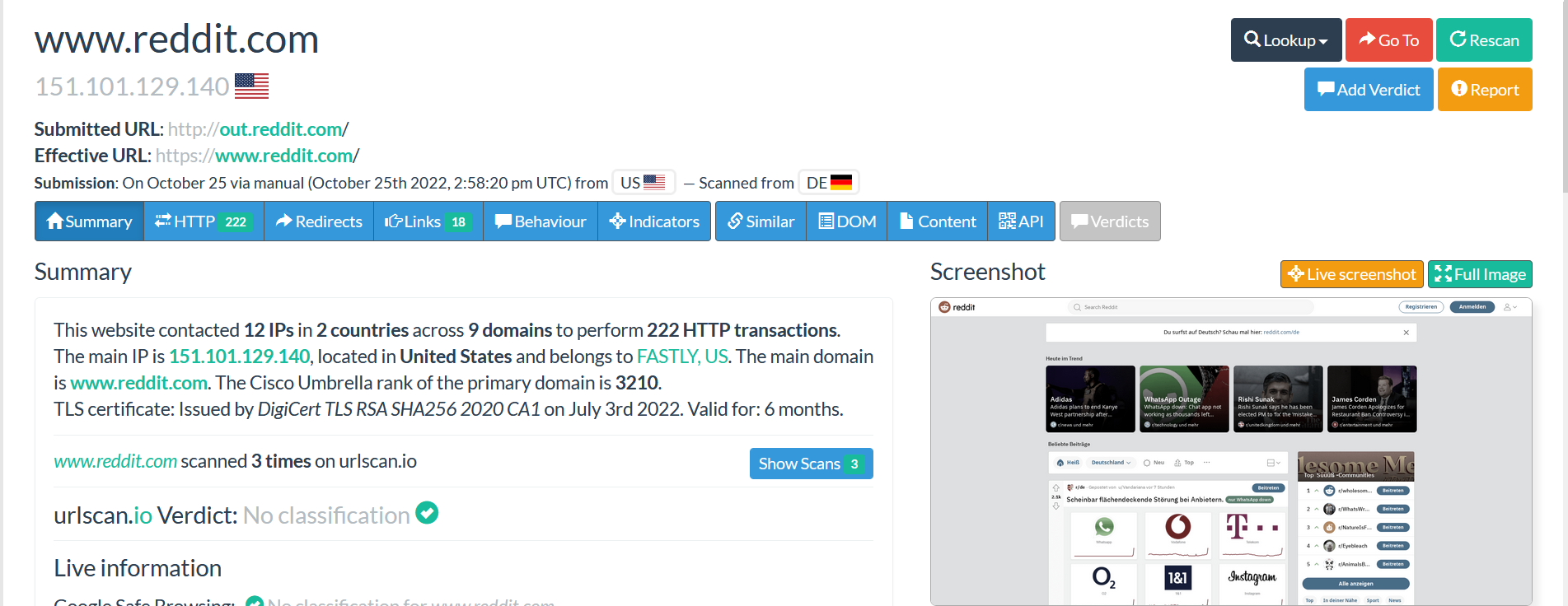
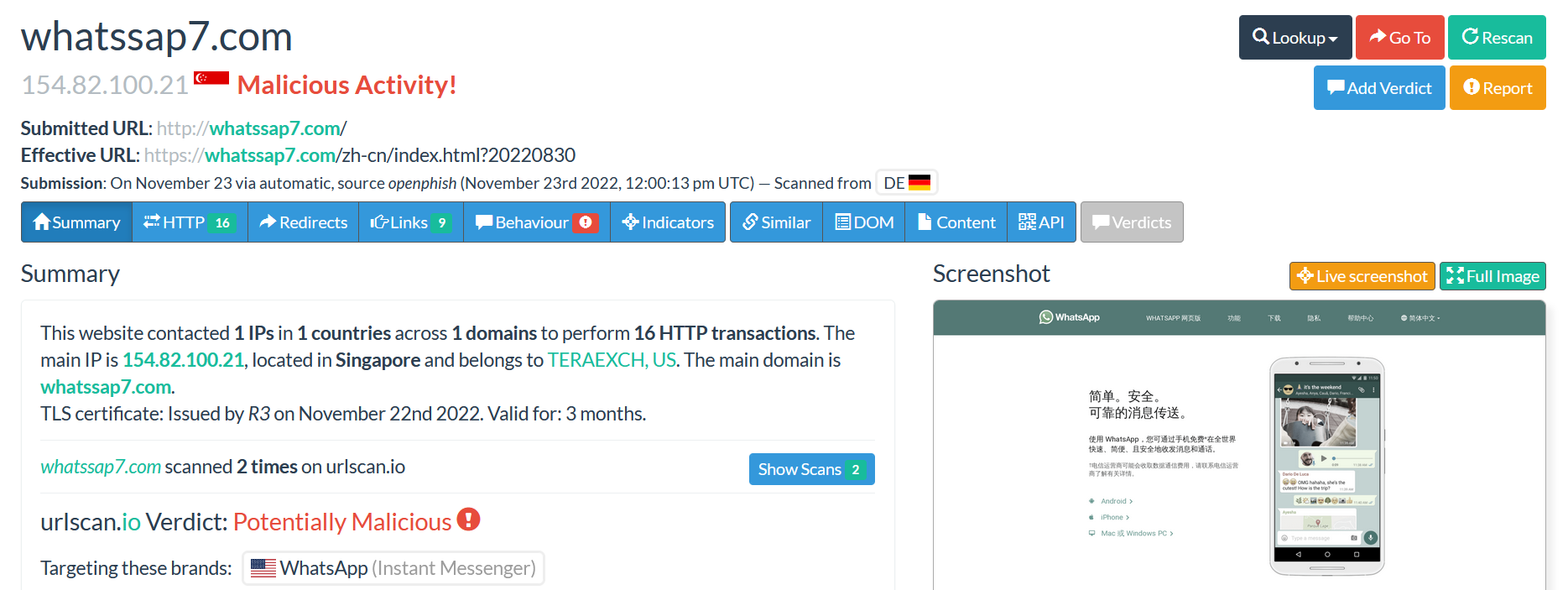
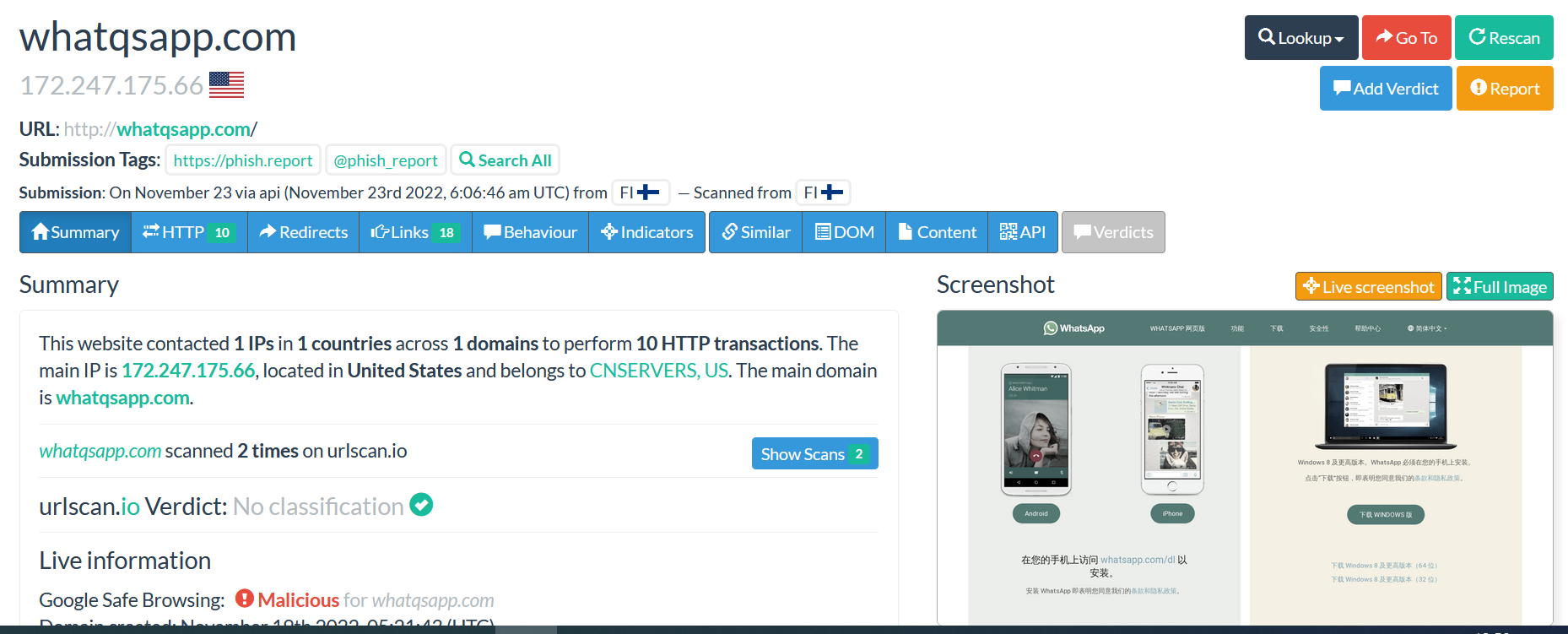
After submitting the URL, we can see the IP address 151.101.129.140 from the submitted URL following the submitted URL and the effective information.
From the right side, we can see 5 menus.

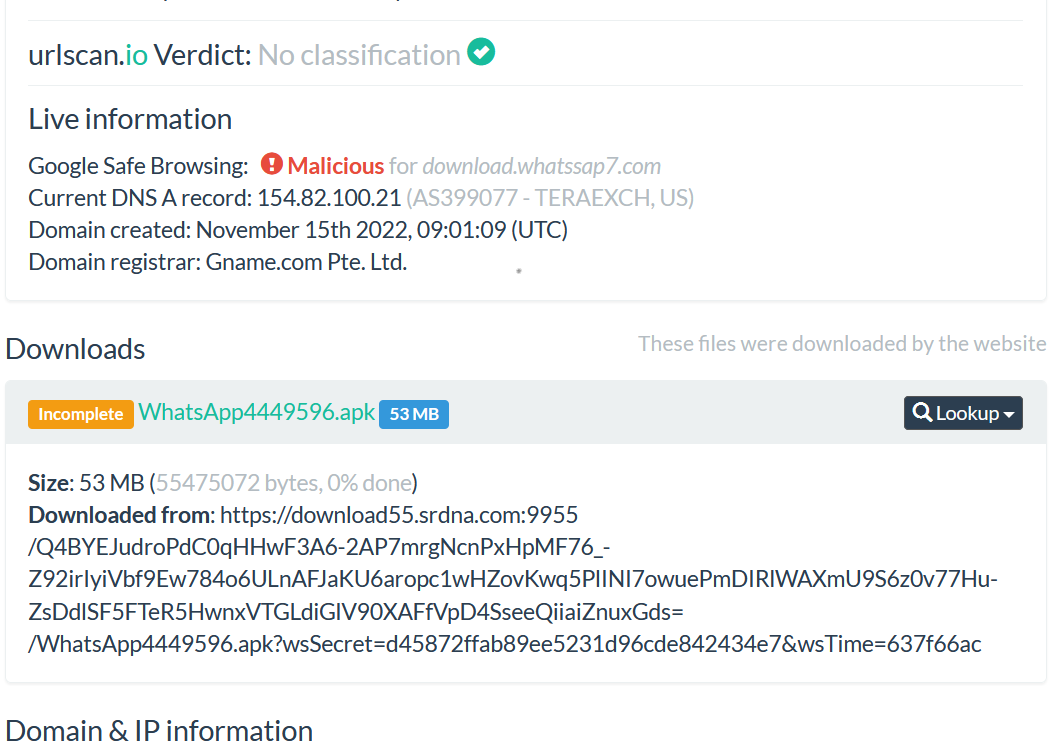
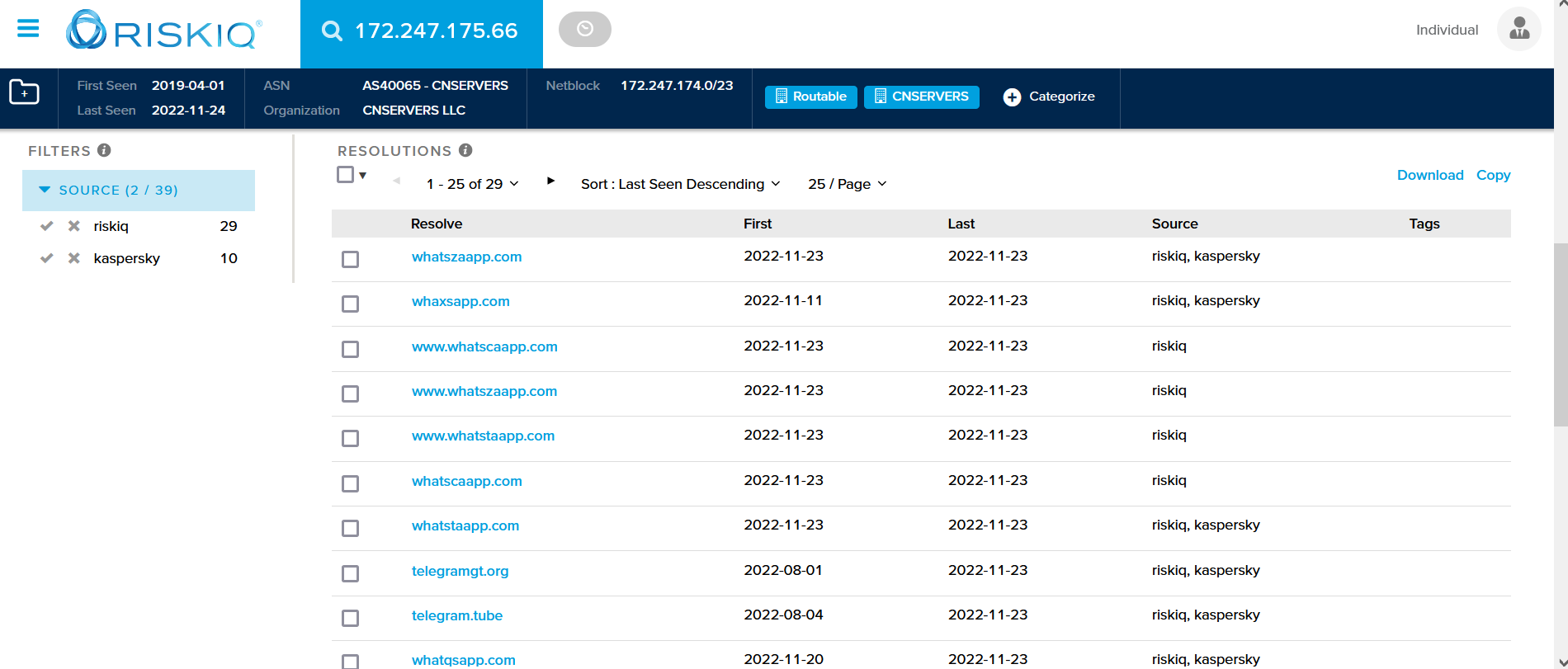
The menu “Lookup” will direct you to find different tools such as (Virus Total, crt.sh, Riskiq …). The tools can help you find more details about the submitted domain (click on each of them to learn more about).
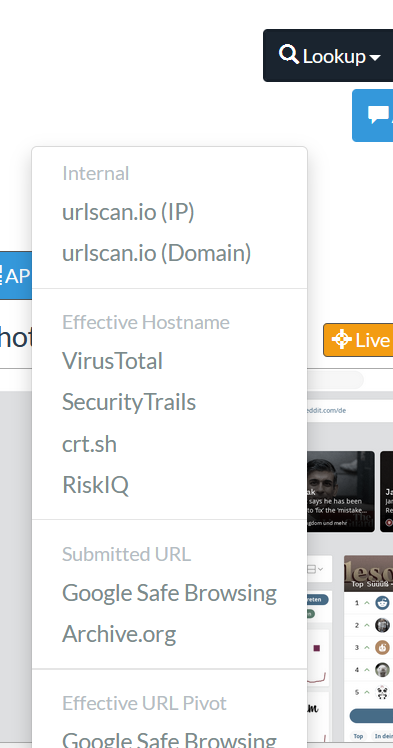
The option “Go To” will bring you to the domain submitted webpage (be careful before you click on it in case it is a malicious domain, you might be compromised).
The option “Rescan” is used to rescan the submitted URL.
The option “Add Verdict” and “Report” are used to add some comments about the submitted domain and contains some details about the scan report.
The next part is described in the part 2 (How to use URLSCAN part2 – osintafrica)
 Best OSINT tools to investigate Typo squatting domains
Best OSINT tools to investigate Typo squatting domains  Top Free Threat Intelligence Feeds for SOC
Top Free Threat Intelligence Feeds for SOC  Best WordPress website scanner for free
Best WordPress website scanner for free  Fake Microsoft Teams website to deliver malware
Fake Microsoft Teams website to deliver malware 













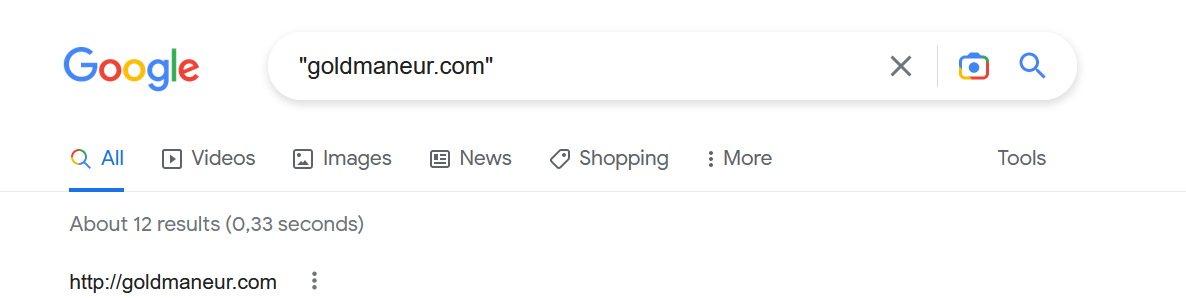
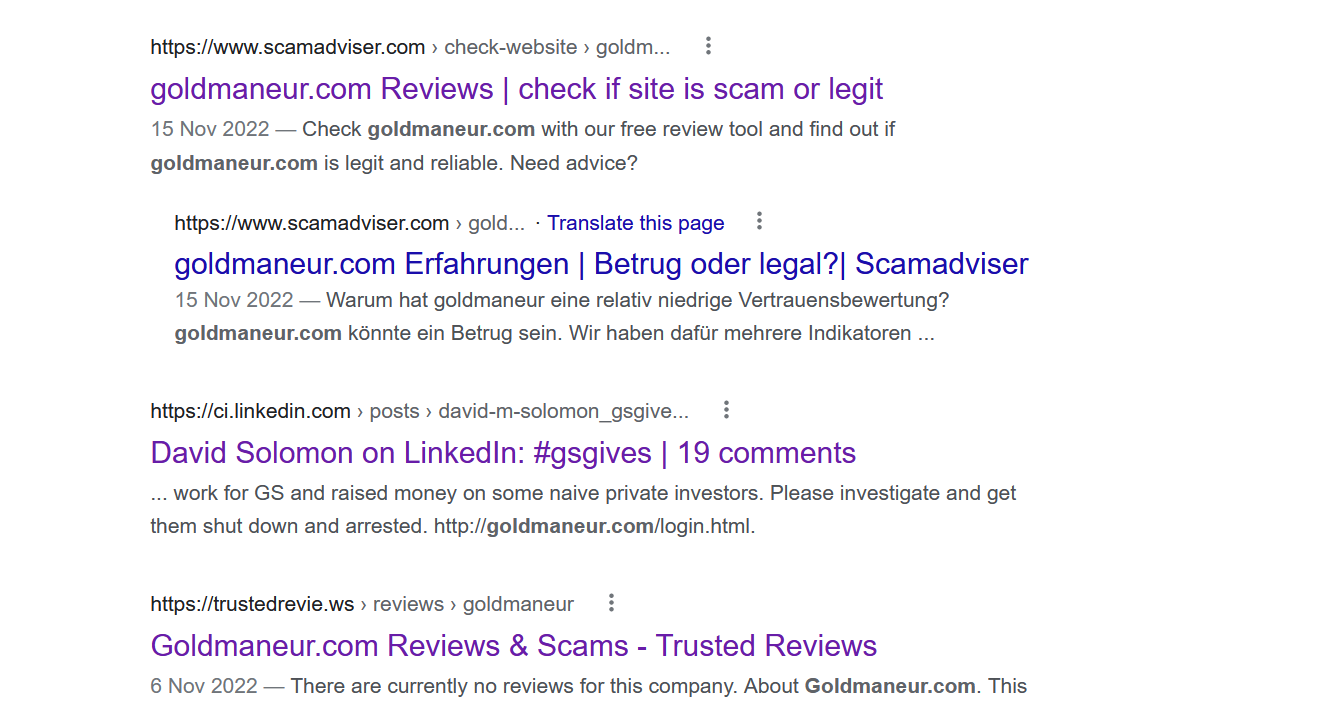
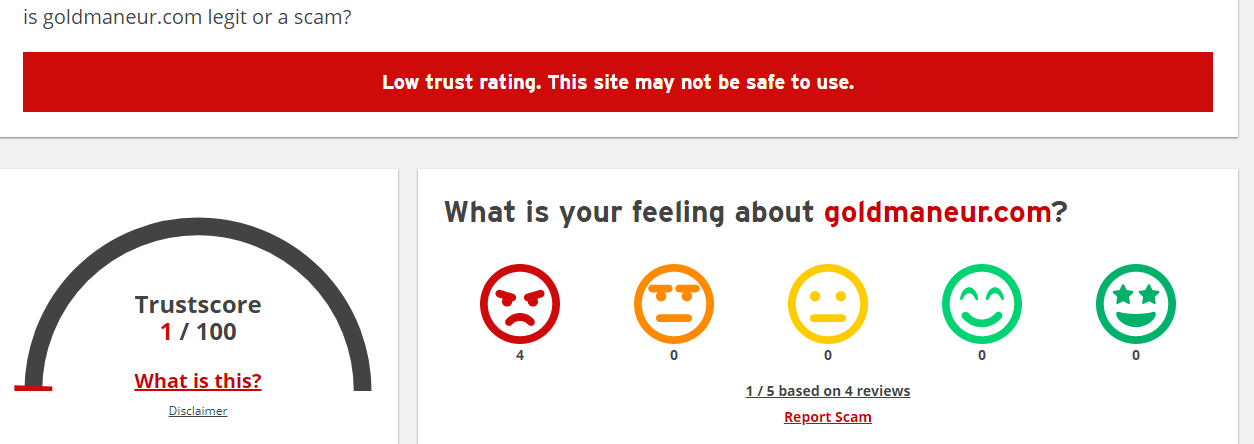
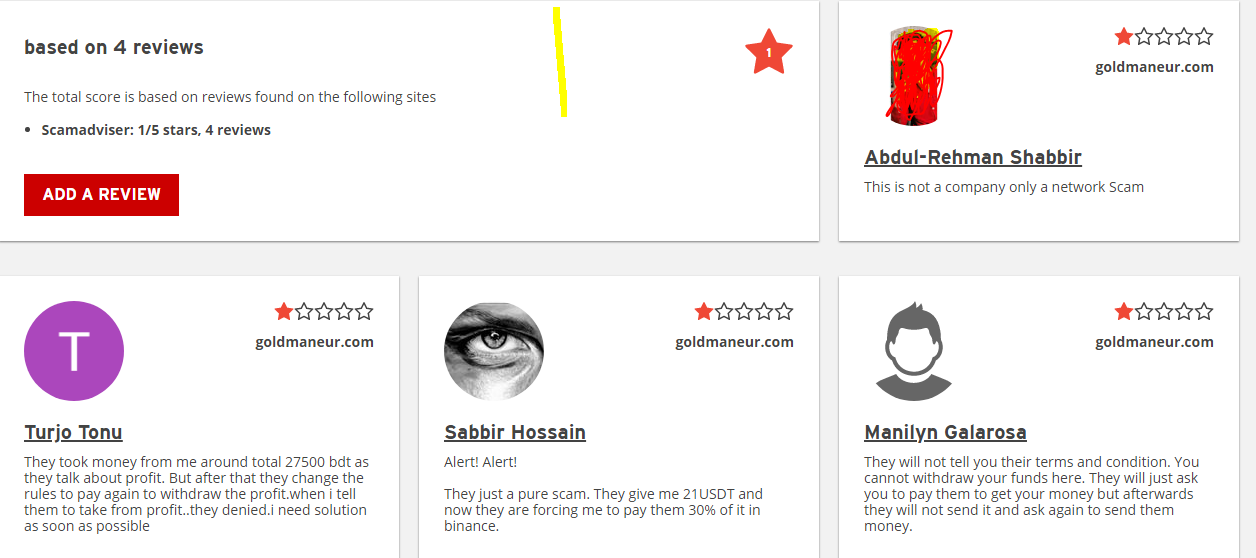
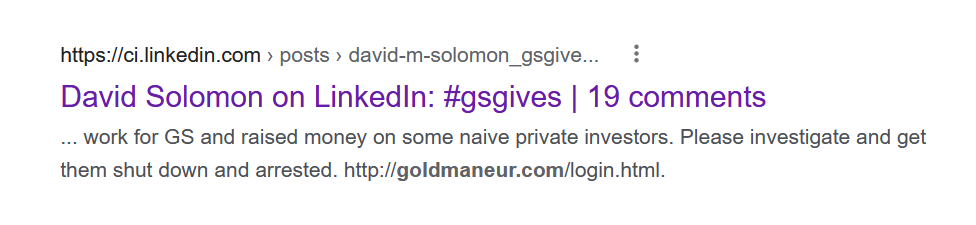
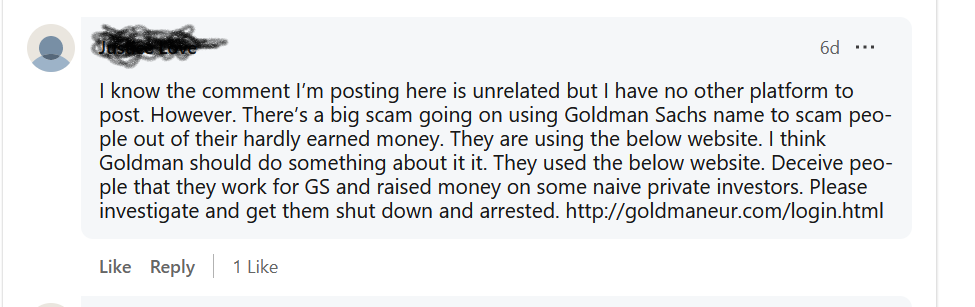
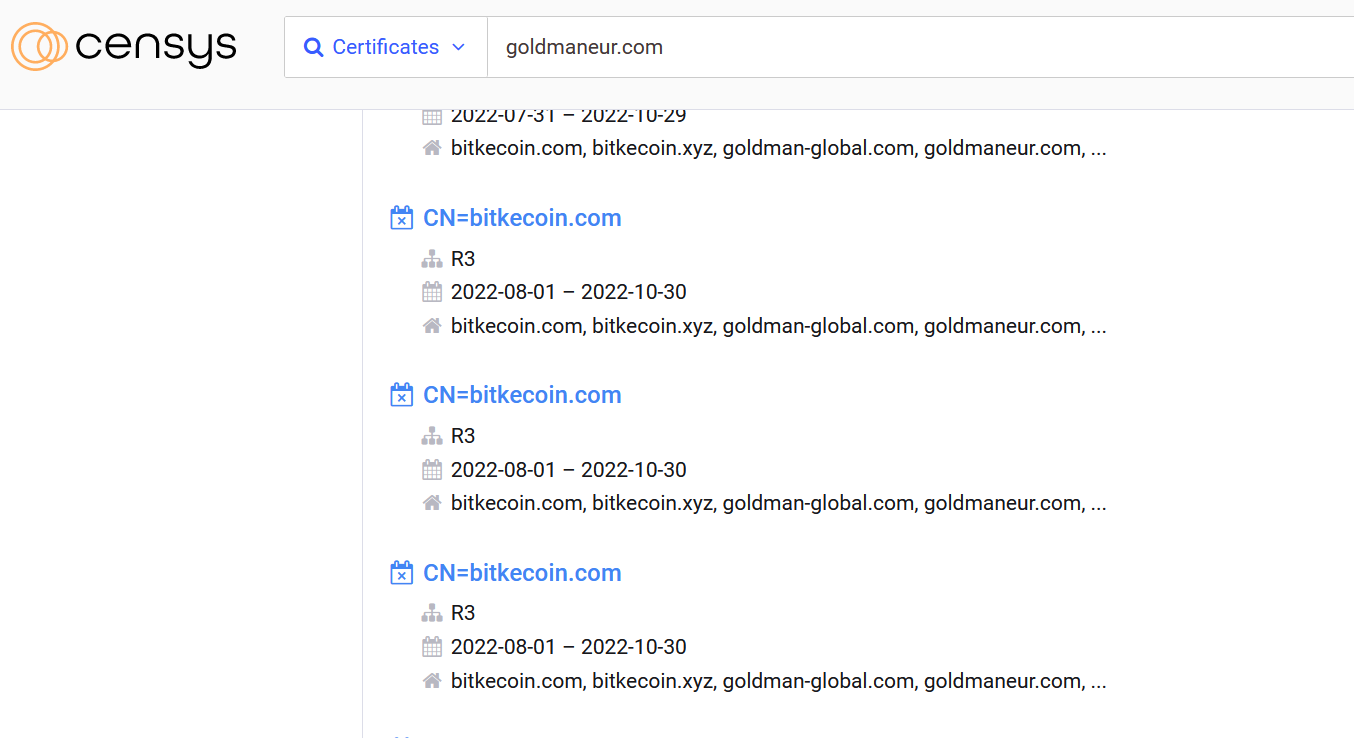
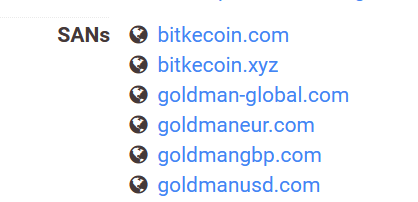
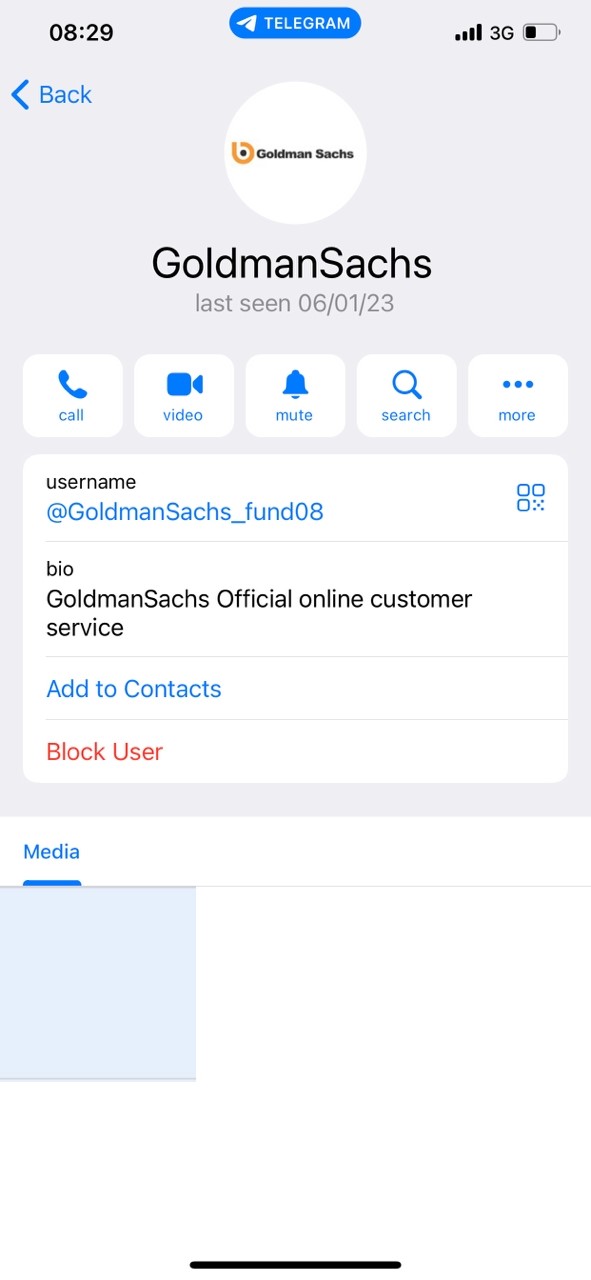

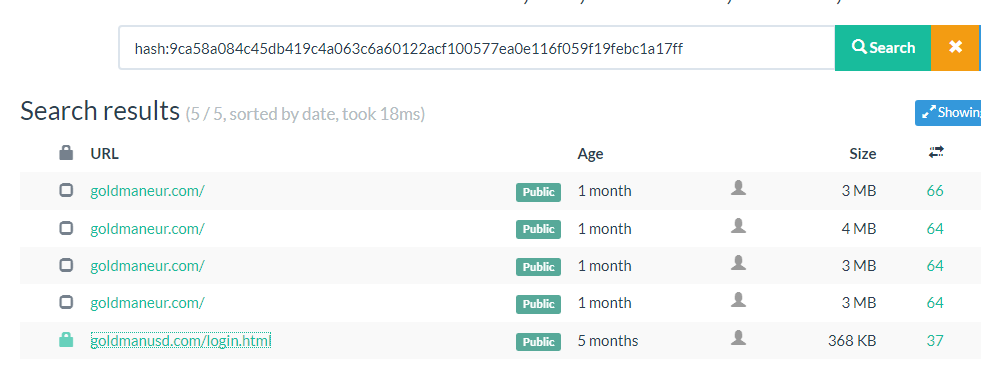






 Imagine a new zero-day vulnerability under exploitation that can impact your organization without a CVE score, and your scanner cannot detect it.
Imagine a new zero-day vulnerability under exploitation that can impact your organization without a CVE score, and your scanner cannot detect it.