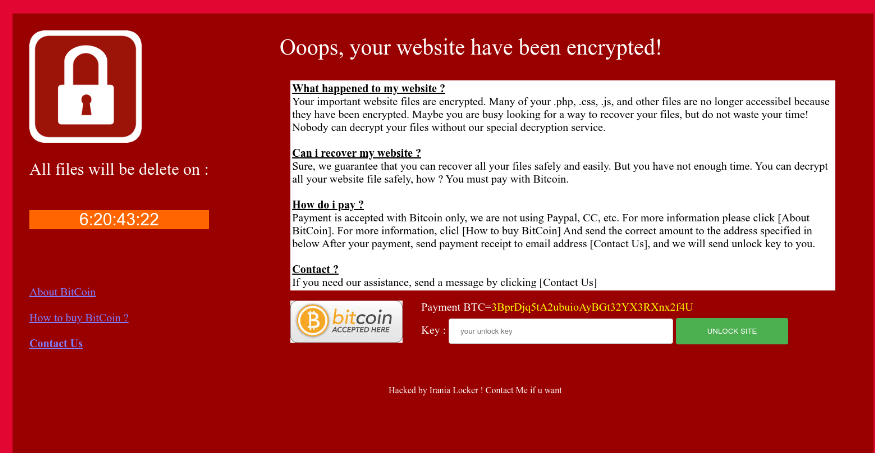
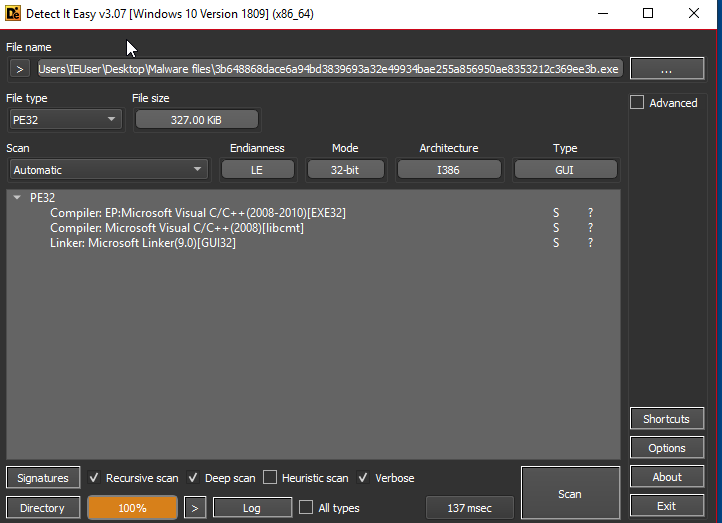
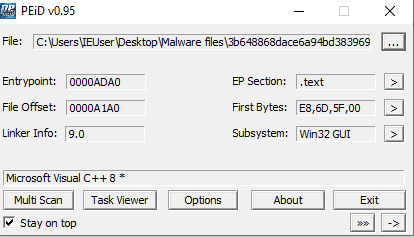
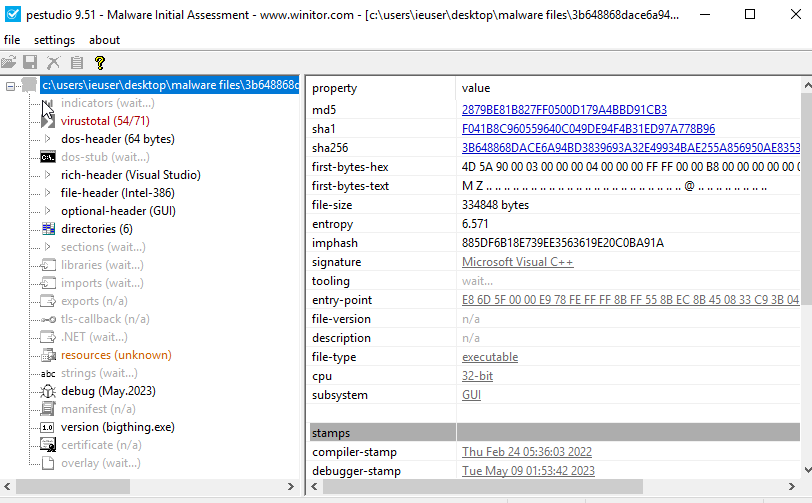
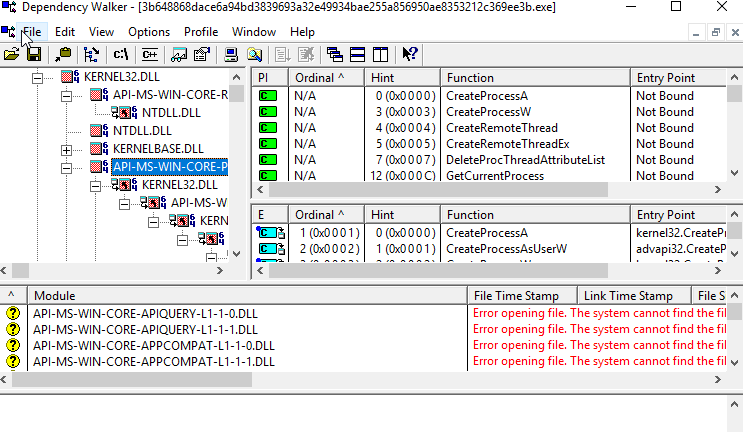
How to use a proxy server for free over the internet
A proxy server is used to protect the network for the following reasons:
Preventing the users to connect to malicious websites
Protecting the company web application by preventing any malicious request that can be used to compromised it
Act as intermediary between the private network and the internet
Can be used to hide the user’s location
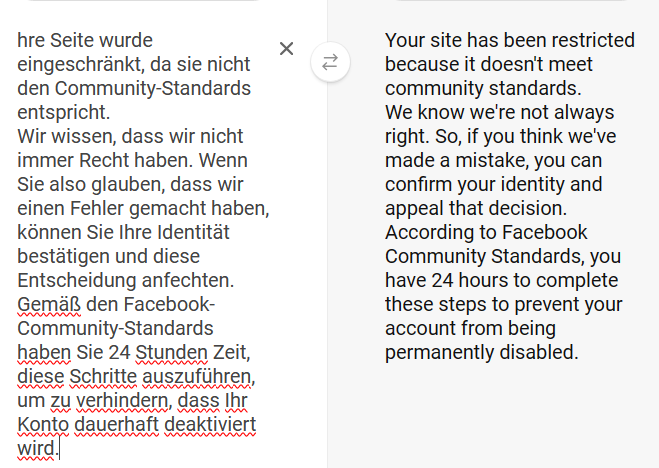
In our example, we will show how you can use a proxy server own by another organization to hide your identity or change your location in order to connect to different web application restricted by the government or the authority.
Over the internet, there are many proxy servers that don’t require any authentication to be used. We will use one of those to show how we can take advantage of it to achieve our goal.
- SPYS
HTTPS proxy list, HTTP proxy with SSL support, free SSL proxy servers (spys.one)
The website is collecting different types of proxy on daily basis. We will use this website to find a proxy server that fits our needs.
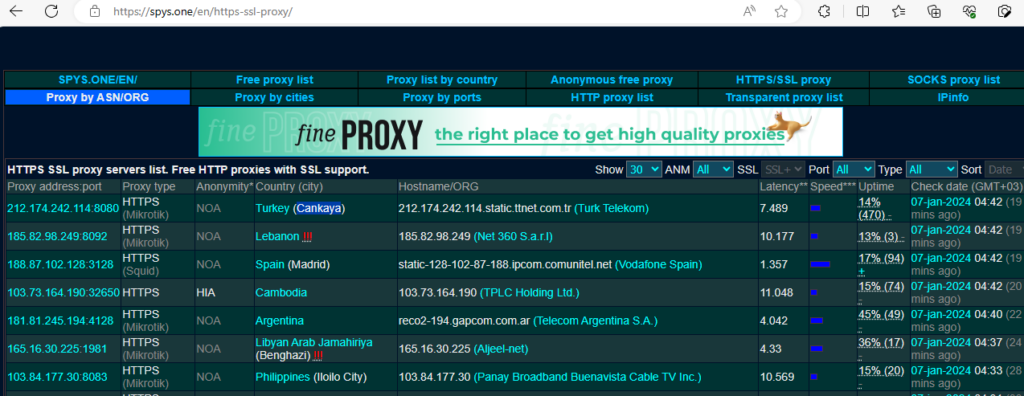
Go to “HTTPS/SSL proxy” choose one proxy with the HTTPS protocol. In our case we choose the proxy server located in Turkey (Cankaya)
Once we find the proper one, now we can start our configuration.
2. CONFIGURATION MODE
In this example, we will use the browser Mozilla.
Open the browser
We need a tool to configure the proxy server. We will install the tool FoxyProxy to manage the proxy.
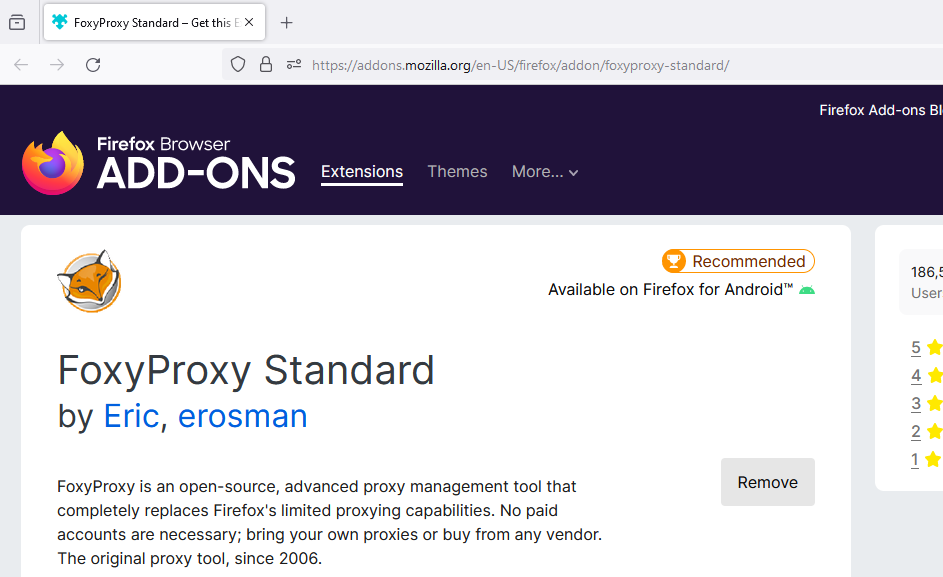
After the installation, the tool will be embedded in Mozilla, click on the “extension” toolbar
The application will be listed, click on “option”, go to “proxies’ menu”
Now, you can start the configuration.
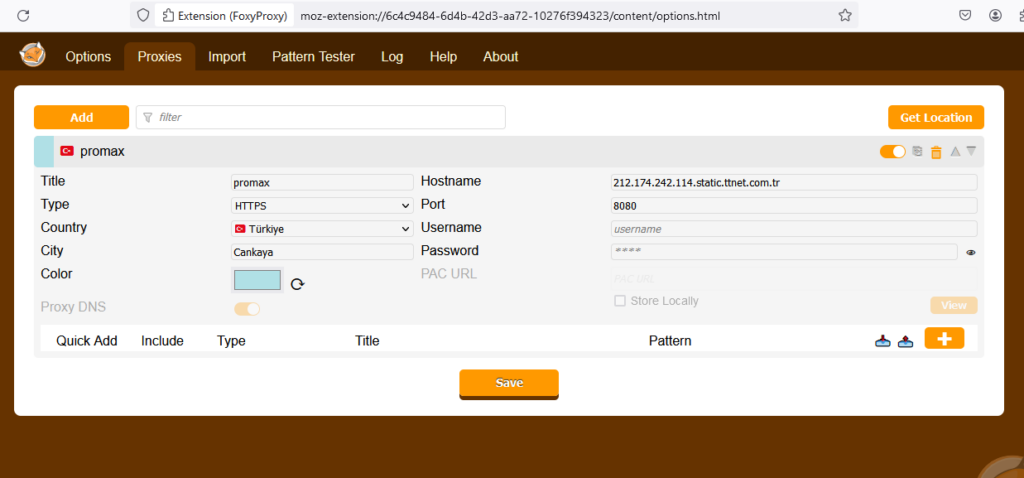
Like you see above, we choose the configuration details from the proxy server “Turkey”, we put all the setting from the proxy.
The last thing to do is to configure our browser
Type in the browser search button: about:preferences#searchResults
Type the IP address and port and chose the HTTPS protocol
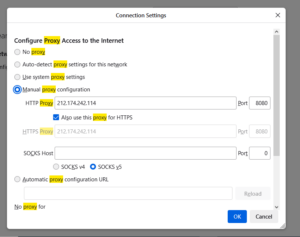
Once done, we can check if the configuration works fine.
https://getfoxyproxy.org/geoip/
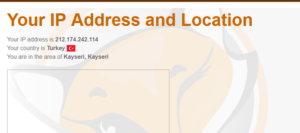
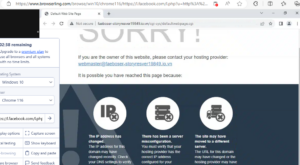
As you see, the location is visible. We can now connect to social media or any other website not restricted in this area.
NB One important thing to mention is that when you use a proxy server from a third party, all you information are passing through his server and know that, it is also not legal to use a proxy server without authorization.