Best OSINT tools to investigate Typo squatting domains
A typo squatting attack is when someone creates a fake website or online service whose name is a misspelled version of a legitimate one, hoping that people will accidentally type it wrong and land on the attacker’s site.
For example, someone might register gooogle.com instead of google.com.
The attacker’s goal can vary:
- Steal passwords or personal info (phishing)
- Install malware
- Show ads or scam offers
- Imitate a real brand to trick users
1. DNSTwister
DNSTwister is a service for generating typo-permutations of a given domain and checking which of those similar domains are actually registered.
It helps detect potential phishing, typosquatting, or domain impersonation risk.
Beyond one-off lookups, it offers monitoring: you can subscribe to have DNSTwister continuously check for new similar domains, or for DNS changes (like MX records).
A company wanting to protect its brand name and domain from phishing: they would register their domain with DNSTwister, and then get notified if someone registers a look-alike domain that could send emails, impersonate them, etc.
More details: DNSTwister.report
2. typosquatting-finder.circl.lu
typosquatting-finder.circl.lu is a free, public service provided by CIRCL (Computer Incident Response Center Luxembourg) to check whether there are existing typo-squatted domains for a given domain.
It’s designed for quick assessment: you enter a domain, and it shows potentially similar (typo) domains.
Typosquatting-finder tries to resolve DNS data (IP, NS, MX) to see which domains are actually registered or resolvable. On the web interface it will show the permutation, IP address, name servers, mail servers, web title, similarity metrics, … depending on what it can find.
More details: Typo-Squatting
3. havebeensquatted.com
Have I Been Squatted is a more fully-featured typosquatting detection and domain monitoring platform.
Its goal is to help individuals and organizations uncover typosquatting, but also to provide continuous protection: not just “are there similar domains now,” but “are there malicious or risky domains being registered and changed over time.”
More details: Have I Been Squatted Documentation — Have I Been Squatted Docs
Typosquatting attacks are a simple but effective form of digital impersonation that exploit small typing mistakes to lure users onto fraudulent websites.
Even though the technique is low-tech, the impact can be serious, ranging from stolen credentials to malware infections or brand damage.
Recommendations to protect against Typosquatting attacks:
- Organizations should regularly scan for look-alike domains
- Use tools that detect suspicious registrations, and educate users about checking URLs carefully.
- Monitoring MX Records to Thwart Phishing Emails
- Quarantine Incoming Emails from Typo squatting Domains
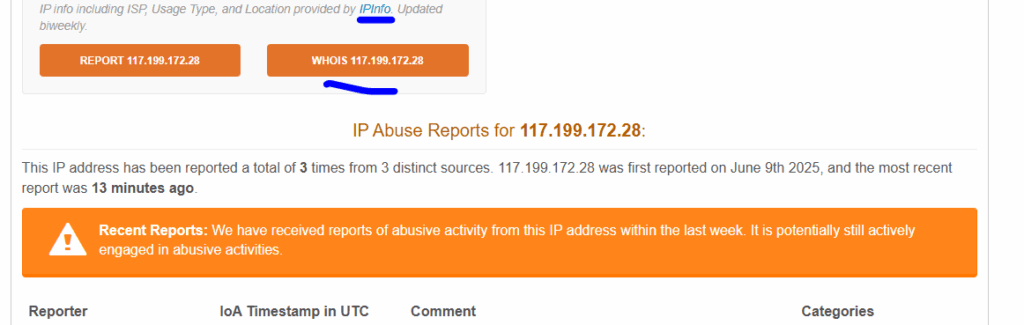
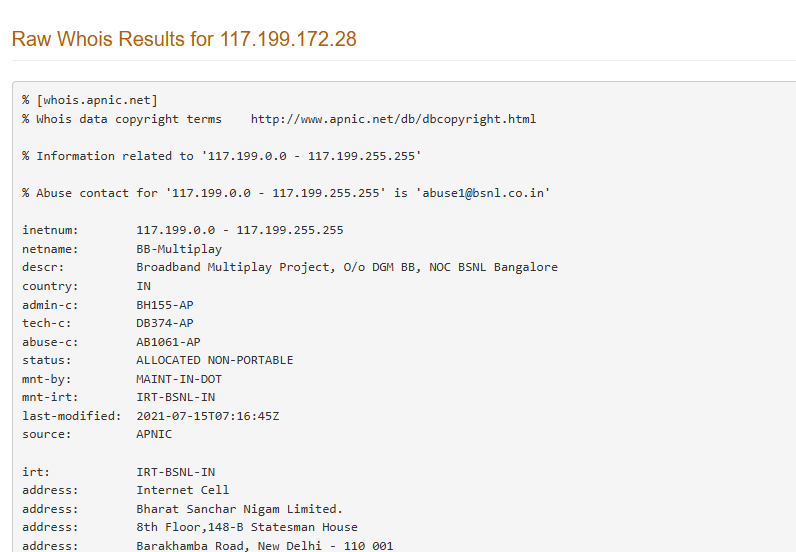
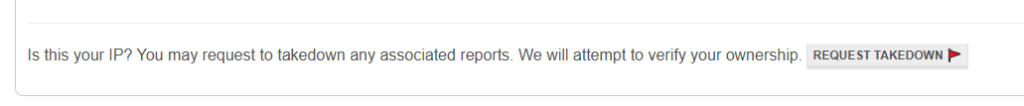
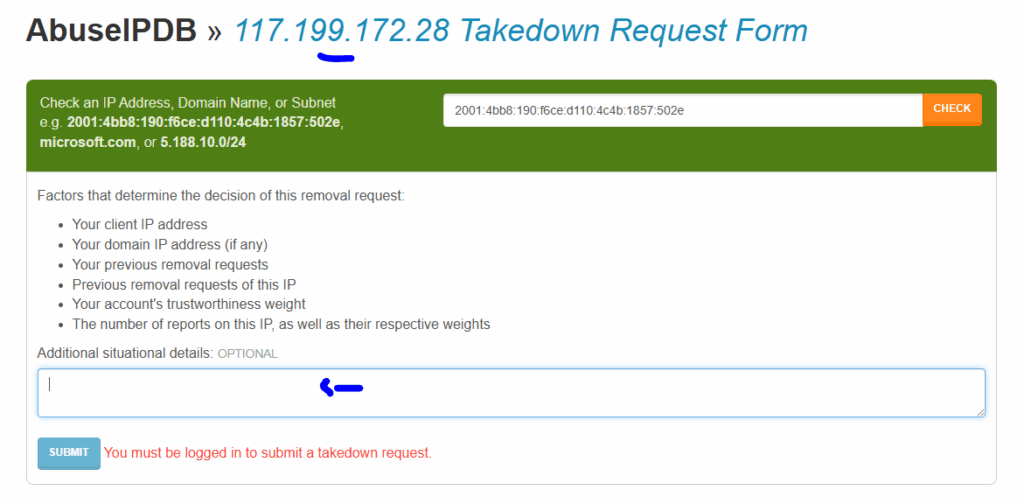
- Request takedowns of the Typo squatting domains
In the end, typo squatting reminds us that even minor lapses in attention can create real security risks, and staying vigilant is a key part of staying safe online.
Always verifying the URL or domain name before you connect to it is the safest way to prevent it.