New update in URLSCAN to detect malicious domains
If you are following our blog Home Home - osintafrica, you already know the tool URL and website scanner - urlscan.io, click on https://www.osintafrica.net/how-to-use-urlscan-part1/ for more details.
The best tools always need improvement and urlscan.io is one of those. The tool has done some improvements that can help an Analyst to perform faster and more efficiently the investigation on phishing website mimicking an organization.
Let’s have a look at the new improvements.
The tool introduced two great features (Favicon hash detection based and the HTTP post request detection) which can be used to detect phishing website mimicking an organization and credentials harvesting domain.
To better understand that, lets practice a bit.
Detecting a website mimicking Netflix using the FAVICON HASH ANALYSIS
A Favicon is the website icon, it helps to visually represent a website and to distinguish between open tabs or search results.
A favicon contains a hash, a hash of a favicon can be used to detect similar website.
The feature has been introduced into urlscan.io to make it easier for the Analyst to quickly perform his or her investigation.
Example 1:
We will connect to urlscan.io and use a domain mimicking NETFLIX website, we will use the favicon hash to find similar website.
Let’s do it.
Connect to https://urlscan.io/result/fb90e947-db87-4476-924d-5db678a50acd/#transactions
Click on the “HTTP” button in blue, type (crtl F - favicon), scroll down, click on the hash and open in a new tab, you will see the result.
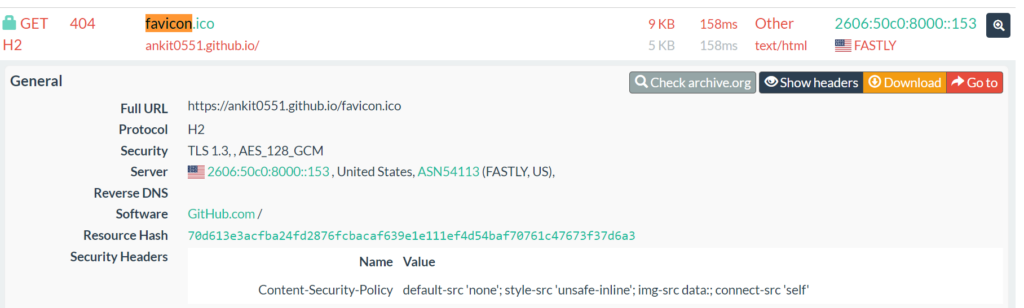
Example 2: Detect website mimicking Microsoft.com.
https://urlscan.io/result/b4cf2f17-ebee-47b4-b85e-f63eae623ec4/#transactions
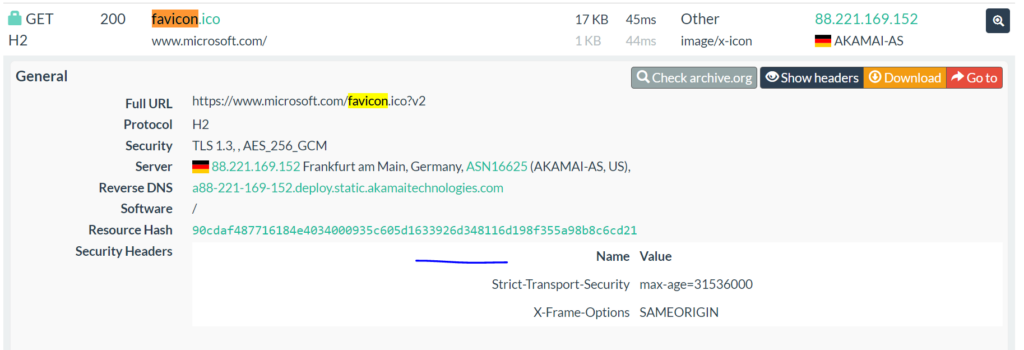
click on the hash and open in a new tab, you will see the result.
Detecting a credential harvesting domain using HTTP POST request detection based.
A credentials harvest is when a threat actor sends a phishing link to user, once the user clicks and enters his/her credentials, the credentials will be sent to another domain, where they will be stored by the threat actor which will be used to impersonate the user or sell via the Dark web. This technic is commonly used against organizations that use the cloud as a service such as Microsoft O365
Let’s give an example, we have detected a maldomain mimicking Microsoft login, when a user enters the credentials, the credentials will be sent to hxxps://robertreed1313[.]xyz/next.php
Click on the link:
https://urlscan.io/result/e25dc1e1-9ab7-491c-94a8-20aec6eba2d8/#transactions
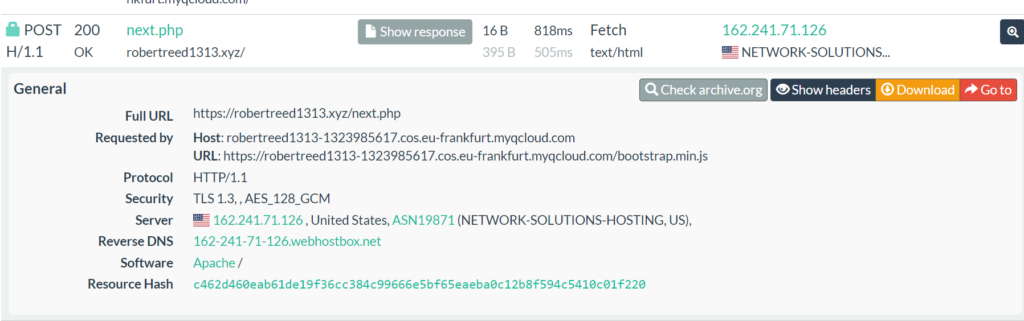
As you see in the image, there is “HTTP POST” request which is an indication of data being sent to another URL in this case (hxxps://robertreed1313[.]xyz/next.php)
Let’s give another example to better understand it.
Another maldomian mimicking Microsoft login website:
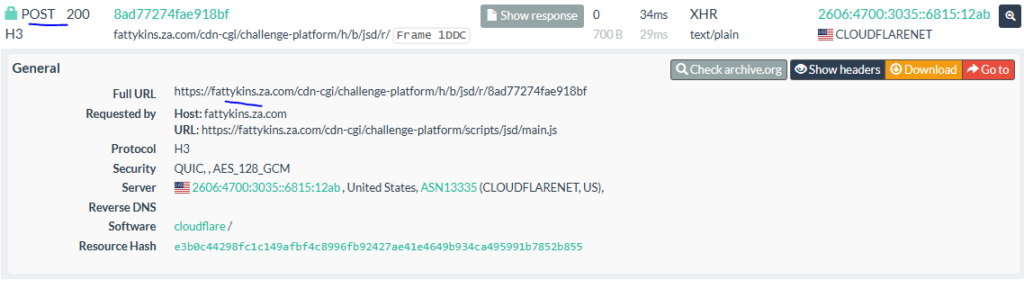
Let’s show the last example
ron-marom12.github.io - urlscan.io
Maldomain mimicking Netflix website login.
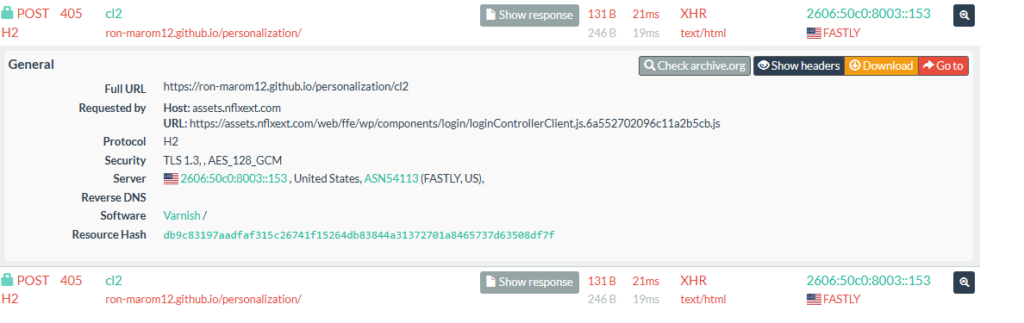
NB: Be careful while checking the domains, always check with Virustotal and check if the domain is newly created before making a decision.
Do you know that we can use URLSCAN to find maldomains or typo squatting domains mimicking our organization?
We will try to find domains name similar to Microsoft.com
Connect to urlscan.io, go to search – type: page.domain:( page.domain:(microsoft.com~ AND NOT microsoft.com))
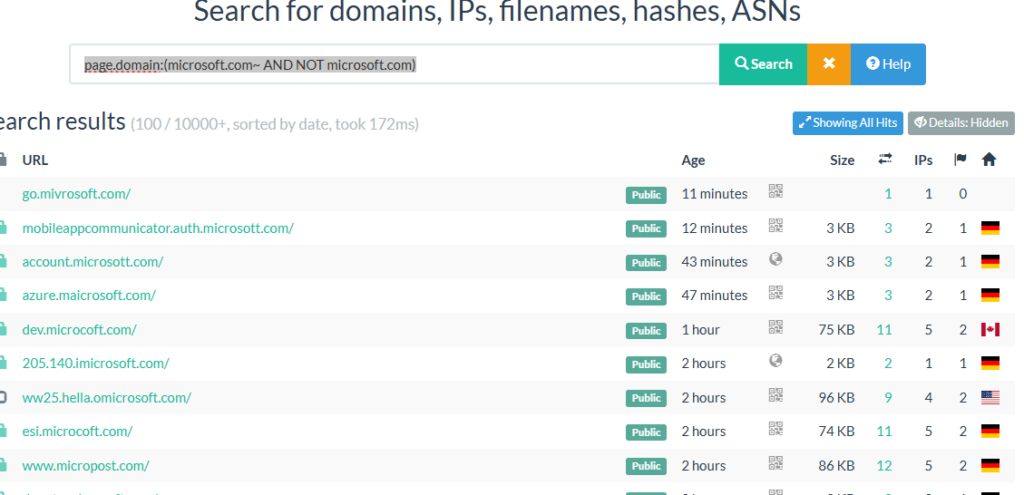
Like you see, URLSCAN has improved a lot; by using the tool, you can save a lot of times during your investigation. Feel free to start using the tool https://urlscan.io/.





